1402 Visual Reference Gallery: IoT Security
1402.1 Visual Reference Gallery
This chapter provides visual references and diagrams for understanding IoT threats, attacks, and security concepts.
1402.2 Source Figures
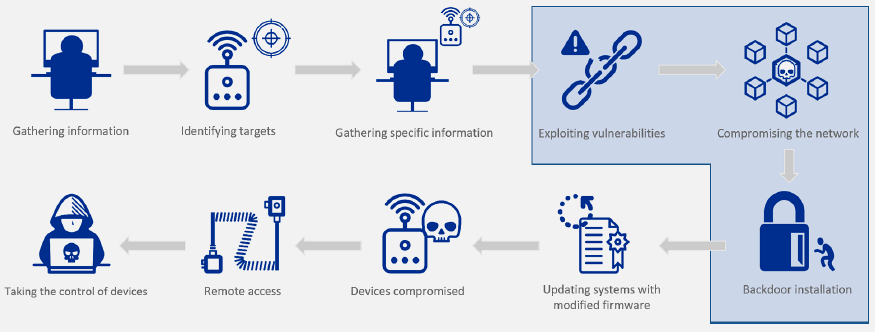
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
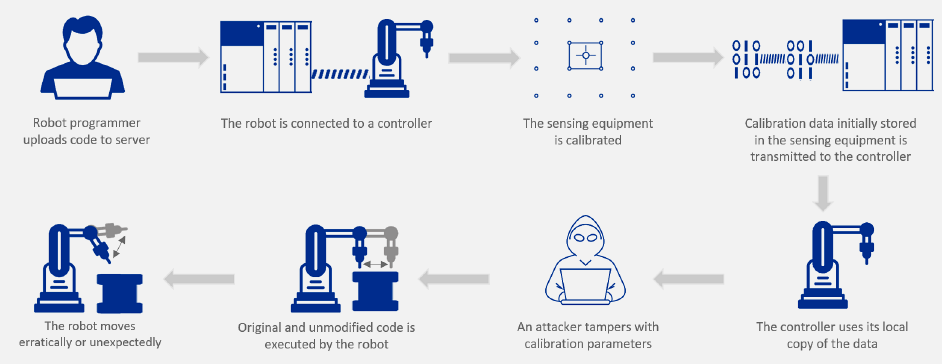
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
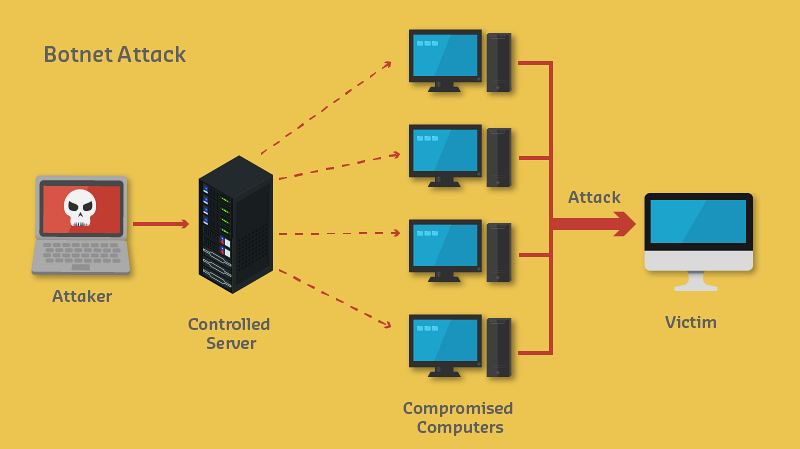
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
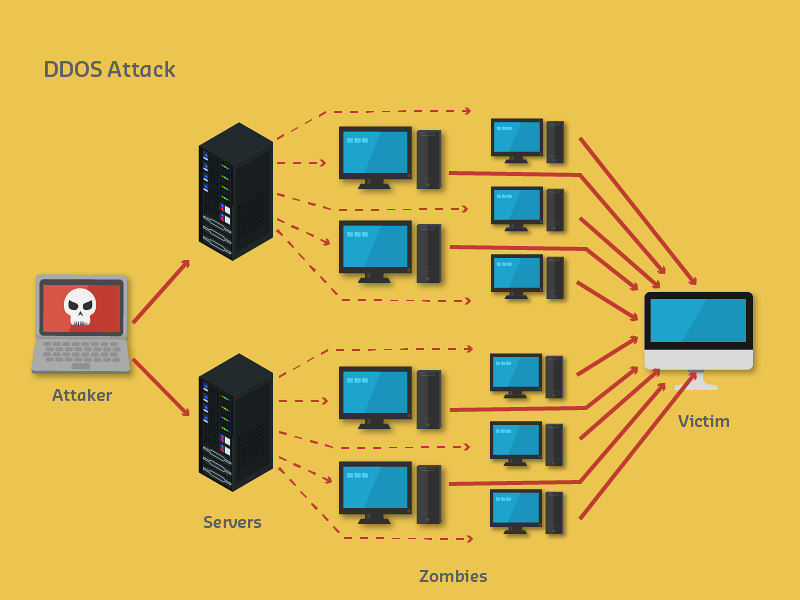
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
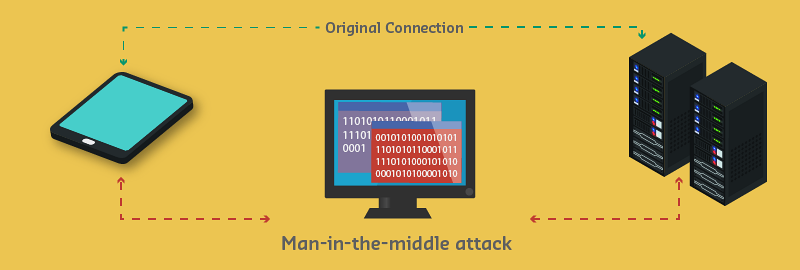
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
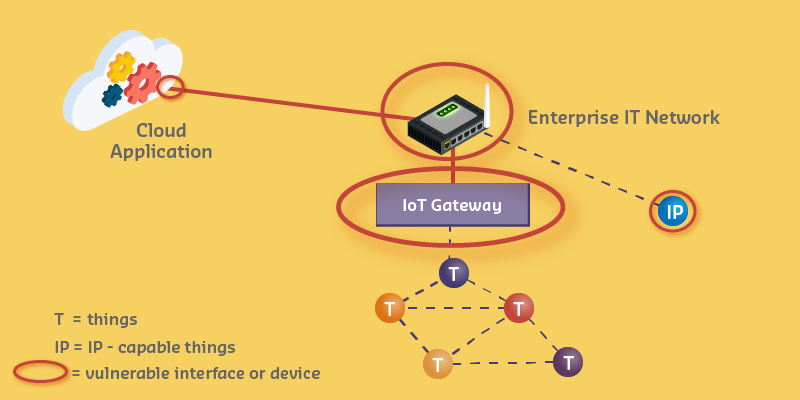
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
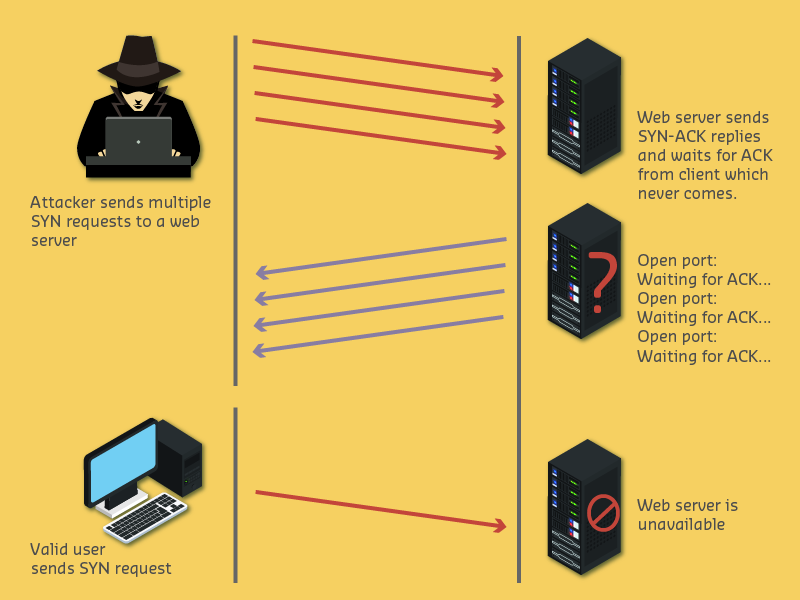
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
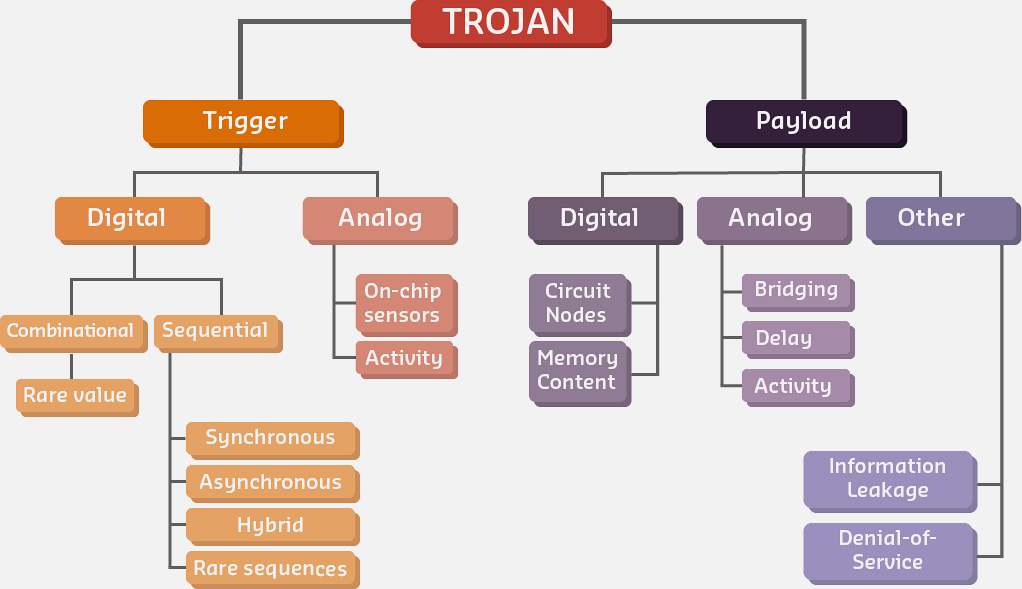
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
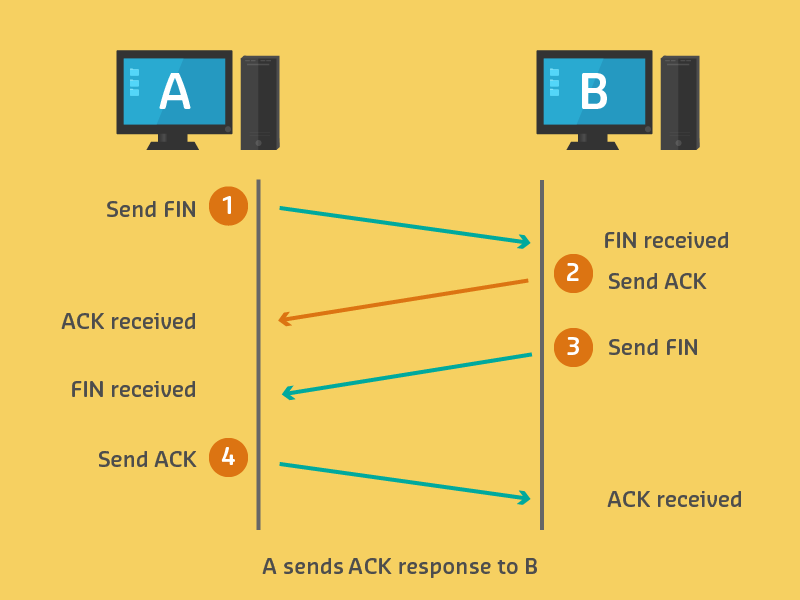
Source: CP IoT System Design Guide, Chapter 6 - Security & Privacy
Security Context: TCP Reset (RST) injection attacks exploit knowledge of this termination sequence by forging RST packets with valid sequence numbers to forcibly disconnect legitimate IoT device sessions.
1402.3 AI-Generated Visualizations
SQL injection remains one of the most dangerous web vulnerabilities, allowing attackers to read, modify, or delete database contents.
Side-channel attacks exploit physical characteristics like power consumption, electromagnetic emissions, or timing to extract secrets from otherwise secure cryptographic implementations.
1402.4 Side-Channel Attack Analysis for IoT
Side-channel attacks bypass cryptographic security by observing physical phenomena during computation. For IoT devices deployed in physically accessible locations, these attacks represent a critical threat.
1402.4.1 Power Analysis Attacks
Simple Power Analysis (SPA): Directly observes power consumption during cryptographic operations. Different instructions consume different power levels, revealing secret key bits.
Differential Power Analysis (DPA): Statistical attack requiring thousands of traces but works even with noisy measurements. With 1,000-10,000 traces, DPA recovers AES keys from unprotected implementations.
1402.4.2 Electromagnetic Analysis (EMA)
EM emissions reveal more localized information than power analysis:
- Can target specific chip areas (isolate crypto unit)
- Works through device enclosures
- Higher signal-to-noise for targeted captures
1402.4.3 Timing Attacks
Execution time variations leak secret-dependent information. Vulnerable implementations include early-exit password comparisons where timing differences reveal correct characters.
1402.4.4 Defense Strategies
| Attack Type | Hardware Defense | Software Defense |
|---|---|---|
| SPA | Shielding, dummy ops | Balanced algorithms |
| DPA | Masking, secure MCU | Higher-order masking |
| EMA | Faraday cage, noise injection | Same as DPA |
| Timing | Constant-time hardware | Constant-time code |
| Cache | Cache partitioning | Flush cache before crypto |
Key Takeaways:
- Assume physical access: Field-deployed devices cannot rely on physical security
- Use certified hardware: FIPS 140-3 Level 3+ includes side-channel resistance
- Limit crypto operations: Rate-limit authentication attempts
- Defense in depth: Combine hardware countermeasures with intrusion detection
1402.5 Summary
IoT threats come from diverse actors using various attack vectors. Key visual concepts:
- STRIDE Model: Spoofing, Tampering, Repudiation, Information Disclosure, DoS, Elevation of Privilege
- Attack Vectors: Physical, network, web/API, firmware, side-channel
- Botnet Architecture: C2 servers directing compromised device networks
- DDoS Patterns: Volumetric, protocol, and application-layer attacks
- Side-Channel: Power, EM, and timing attacks on cryptographic operations
1402.6 What’s Next
Continue exploring IoT security topics:
- Threat Modeling and STRIDE - Apply systematic threat identification
- OWASP IoT Top 10 - Understand critical vulnerabilities
- Interactive Security Tools - Use risk calculators
- Practice Exercises - Apply your knowledge
