%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
graph TB
subgraph P2P["Peer-to-Peer Mode"]
P1[Active Device A<br/>Phone] <-->|Bidirectional<br/>424 kbps| P2[Active Device B<br/>Phone]
P_USE[File sharing<br/>Contact exchange]
end
subgraph RW["Reader/Writer Mode"]
R1[Active Reader<br/>Phone/Terminal] -->|Powers tag<br/>Read/Write| T1[Passive Tag<br/>NTAG/MIFARE]
RW_USE[Smart posters<br/>Product info]
end
subgraph CE["Card Emulation Mode"]
C1[Active Terminal<br/>POS/Reader] -->|Reads phone<br/>as card| C2[Phone as Card<br/>Secure Element]
CE_USE[Mobile payments<br/>Access control]
end
style P2P fill:#16A085,stroke:#2C3E50,stroke-width:2px
style RW fill:#E67E22,stroke:#2C3E50,stroke-width:2px
style CE fill:#2C3E50,stroke:#16A085,stroke-width:2px
style P1 fill:#2C3E50,stroke:#16A085,color:#fff
style P2 fill:#2C3E50,stroke:#16A085,color:#fff
style R1 fill:#E67E22,stroke:#2C3E50,color:#fff
style T1 fill:#7F8C8D,stroke:#2C3E50,color:#fff
style C1 fill:#16A085,stroke:#2C3E50,color:#fff
style C2 fill:#2C3E50,stroke:#16A085,color:#fff
877 NFC Communication Fundamentals
877.1 Learning Objectives
By the end of this chapter, you will be able to:
- Understand NFC Fundamentals: Explain what NFC is and how it differs from RFID
- Identify Operating Modes: Describe peer-to-peer, read/write, and card emulation modes
- Understand Tag Types: Select appropriate NFC tag types for different applications
- Master NDEF Format: Structure data using NFC Data Exchange Format
877.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Network Access and Physical Layer Protocols: Understanding physical layer concepts and short-range wireless technologies provides context for NFC’s operating principles and 13.56 MHz frequency band
- Networking Basics: Basic knowledge of communication protocols and data exchange helps you understand NFC’s peer-to-peer and reader/writer modes
NFC Deep Dives: - NFC Implementation and Applications - Hands-on tag programming - NFC IoT Integration - IoT ecosystems and labs - NFC Security and Comparisons - Security and technology comparisons
Related Protocols: - RFID Fundamentals - Understanding the parent technology - Bluetooth Fundamentals - Alternative short-range protocol
Have you ever tapped your phone to pay at a store, or touched your phone to a poster to get more information? That’s Near Field Communication (NFC) in action. NFC is a wireless technology that works over very short distances—typically just a few centimeters (about 1-2 inches).
Think of NFC as a “digital handshake” between two devices when they touch or get very close. Unlike Wi-Fi or Bluetooth that can work across a room, NFC requires devices to be almost touching. This short range helps reduce risk and makes the tap interaction intentional (though attacks like relays are still possible in some threat models).
How is NFC used in IoT?
NFC has three main modes: reading tags (like scanning a smart poster), card emulation (your phone pretending to be a credit card), and peer-to-peer (two phones sharing data by tapping). In IoT, NFC is perfect for configuration (tap phone to sensor to set it up), identification (tap badge to unlock door), and quick data exchange (tap phone to smart home device to control it).
The beauty of NFC is that simple NFC tags need no battery—they’re powered by the radio waves from your phone when you bring it close. This makes NFC tags incredibly cheap (10-50 cents each) and they last forever since there’s no battery to die.
| Term | Simple Explanation |
|---|---|
| NFC (Near Field Communication) | Wireless technology for very short-range communication (1-10 cm) |
| Tag | Passive device (no battery) that stores data readable by NFC phones |
| Reader | Active device (like smartphone) that powers and reads NFC tags |
| 13.56 MHz | Radio frequency NFC uses—part of High Frequency (HF) RFID band |
| Passive Tag | Tag with no battery—powered by reader’s radio waves |
| Active Device | Device with battery that can generate its own radio field |
| NDEF | NFC Data Exchange Format—standard way to structure data on tags |
| Peer-to-Peer Mode | Two active devices exchanging data (phone-to-phone) |
877.3 What is NFC?
Test your understanding of these NFC concepts.
877.4 Definition
NFC (Near Field Communication) is a short-range wireless technology based on HF RFID that enables two devices to communicate when brought within 4-10 cm of each other. Operating at 13.56 MHz, NFC provides secure, intuitive touch-to-connect interactions for payments, access control, data transfer, and device pairing.
Key Characteristics:
- Range: 4-10 cm (intentionally short for security)
- Frequency: 13.56 MHz (HF)

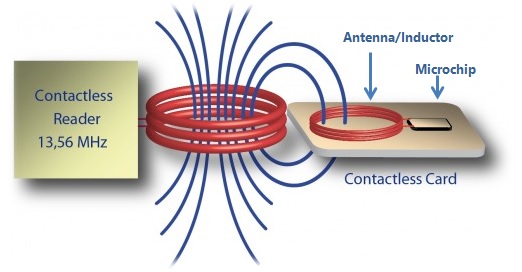
- Data Rate: 106, 212, 424, or 848 Kbps
- Power: Passive tags powered by reader field
- Bi-directional: Can both send and receive data
- Ubiquitous: Built into 2+ billion smartphones globally
877.5 NFC vs RFID: Understanding the Relationship
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart TD
RFID[RFID Technology<br/>13.56 MHz - UHF]
RFID --> LF[LF: 125 kHz<br/>Access Control]
RFID --> HF[HF: 13.56 MHz<br/>Smart Cards, NFC]
RFID --> UHF[UHF: 860-960 MHz<br/>Supply Chain]
HF --> NFC[NFC Subset<br/>13.56 MHz, <10 cm]
NFC --> P2P[Peer-to-Peer<br/>Device to Device]
NFC --> RW[Read/Write<br/>Tag Interaction]
NFC --> CE[Card Emulation<br/>Mobile Payments]
style RFID fill:#7F8C8D,stroke:#333,color:#fff
style HF fill:#16A085,stroke:#2C3E50,color:#fff
style NFC fill:#2C3E50,stroke:#16A085,color:#fff
style P2P fill:#E67E22,stroke:#2C3E50,color:#fff
style RW fill:#E67E22,stroke:#2C3E50,color:#fff
style CE fill:#E67E22,stroke:#2C3E50,color:#fff
NFC is a subset of HF RFID (13.56 MHz) with added capabilities:
What makes NFC different: - ✅ Peer-to-peer mode: Two active devices can exchange data - ✅ Card emulation: Phone can act like contactless card - ✅ Built into smartphones: Billions of NFC-enabled devices - ✅ User-initiated: Intentional touch-to-connect experience - ✅ Standardized protocols: NDEF data format for interoperability
| Feature | RFID (General) | NFC |
|---|---|---|
| Frequency | LF, HF, UHF, Microwave | HF only (13.56 MHz) |
| Range | cm to 10m+ | 4-10 cm (intentionally short) |
| Modes | Read-only typically | Peer-to-peer, read/write, emulation |
| Devices | Specialized readers | Smartphones, tablets, wearables |
| Use Cases | Inventory, logistics, access | Payments, pairing, smart marketing |
| Standards | ISO 14443, 15693, 18000 | ISO 14443, ISO 18092, NFC Forum |
877.6 How NFC Works
877.6.1 Basic Operating Principle
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
sequenceDiagram
participant I as Initiator<br/>(Active Device)
participant T as Target<br/>(Passive Tag/Device)
I->>T: RF Field (13.56 MHz)
Note over T: Powers up via<br/>electromagnetic induction
I->>T: Modulated Signal<br/>(Command/Data)
T->>I: Load Modulation<br/>(Response Data)
Note over I,T: Bidirectional<br/>Communication
NFC Communication:
- Proximity detection: Devices come within 4-10 cm
- Field generation: Active device creates 13.56 MHz field
- Power transfer: Passive tag harvests energy from field
- Data exchange: Bi-directional communication via load modulation
- Action: Payment, data transfer, or configuration triggered
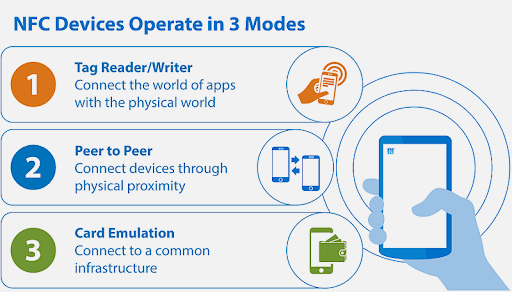
877.7 NFC Operating Modes
NFC supports three distinct operating modes, making it more versatile than traditional RFID:
877.7.1 Peer-to-Peer Mode
Two active NFC devices exchange data
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart LR
Phone1[Phone 1<br/>Active] <-->|NFC P2P<br/>424 kbps| Phone2[Phone 2<br/>Active]
Phone1 -.->|Share Contact| Phone2
Phone1 -.->|Share Photo| Phone2
Phone1 -.->|Wi-Fi Setup| Phone2
style Phone1 fill:#2C3E50,stroke:#16A085,color:#fff
style Phone2 fill:#16A085,stroke:#2C3E50,color:#fff
Use Cases: - File sharing: Photos, contacts, documents between phones - Bluetooth pairing: Touch phones to pair speakers/headphones - Gaming: Transfer game data between devices - Business cards: Exchange contact info
Protocol: ISO 18092 (NFCIP-1)
Example: Android Beam (deprecated but illustrative)
// Share data via NFC P2P
NfcAdapter nfcAdapter = NfcAdapter.getDefaultAdapter(this);
nfcAdapter.setNdefPushMessage(message, this);877.7.2 Read/Write Mode
Active device reads from or writes to passive NFC tag
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart LR
Phone[Smartphone<br/>Active Reader] -->|Read Data| Tag1[Smart Poster<br/>Passive Tag]
Phone -->|Write URL| Tag2[Programmable Tag<br/>NTAG215]
Tag1 -.->|URL, Text, Wi-Fi| Phone
Phone -.->|Store Config| Tag2
style Phone fill:#2C3E50,stroke:#16A085,color:#fff
style Tag1 fill:#16A085,stroke:#2C3E50,color:#fff
style Tag2 fill:#E67E22,stroke:#2C3E50,color:#fff
Use Cases: - Smart posters: Tap tag to open URL, download app - Product information: Get details, reviews, instructions - Home automation: Tap tag to trigger IoT scene - Museum exhibits: Interactive information displays - Inventory: Track and update asset information
Tag Types: - Type 1-5 (different memory sizes and capabilities) - Writable (can update content) - Read-only (locked after writing)
877.7.3 Card Emulation Mode
Active device emulates a contactless smart card
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart LR
Phone[Smartphone<br/>Emulates Card] -->|NFC Tap| Terminal[Payment Terminal<br/>Active Reader]
Terminal -->|Request Payment| Phone
Phone -->|Token + Crypto| Terminal
Terminal -->|Validate| Bank[Bank Server]
style Phone fill:#2C3E50,stroke:#16A085,color:#fff
style Terminal fill:#16A085,stroke:#2C3E50,color:#fff
style Bank fill:#E67E22,stroke:#2C3E50,color:#fff
Use Cases: - Mobile payments: Apple Pay, Google Pay, Samsung Pay - Transit ticketing: Subway/bus tap-to-pay - Access control: Phone as building/hotel key - Loyalty cards: Digital membership cards
Technologies: - HCE (Host Card Emulation): Software-based, uses phone CPU - SIM-based: Secure element in SIM card - Embedded SE: Dedicated secure chip in phone
877.8 NFC Tag Types
NFC tags come in different types with varying memory and capabilities:
| Type | Memory | Speed | Rewritable | Use Case | Example |
|---|---|---|---|---|---|
| Type 1 | 96 bytes - 2 KB | 106 Kbps | Yes | Simple marketing | Topaz |
| Type 2 | 48 bytes - 2 KB | 106 Kbps | Yes | Smart posters | MIFARE Ultralight |
| Type 3 | Variable | 212 Kbps | Yes/No | Transit, eSIM | Sony FeliCa |
| Type 4 | 4 KB - 32 KB | 424 Kbps | Yes | High-security | MIFARE DESFire |
| Type 5 | 256 bytes - 8 KB | 106 Kbps | Yes | IoT sensors | ISO 15693 |
For simple tasks (URL, text): Type 2 (cheap, ~$0.20) For payments, access: Type 4 (secure, encrypted) For IoT sensors: Type 5 (longer range within NFC spec) For read-only: Lock Type 2 after writing
877.9 NDEF (NFC Data Exchange Format)
NDEF is the standard data format for NFC, ensuring interoperability between devices.
877.9.1 NDEF Message Structure
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart TD
MSG[NDEF Message] --> REC1[Record 1<br/>Header + Payload]
MSG --> REC2[Record 2<br/>Header + Payload]
MSG --> REC3[Record 3<br/>Header + Payload]
REC1 --> H1[Header<br/>TNF, Type, ID, Flags]
REC1 --> P1[Payload<br/>URL: https://example.com]
REC2 --> H2[Header<br/>TNF, Type, ID, Flags]
REC2 --> P2[Payload<br/>Text: Hello NFC]
style MSG fill:#2C3E50,stroke:#16A085,color:#fff
style REC1 fill:#16A085,stroke:#2C3E50,color:#fff
style REC2 fill:#16A085,stroke:#2C3E50,color:#fff
style REC3 fill:#7F8C8D,stroke:#333,color:#fff
877.9.2 Common NDEF Record Types
URI Record (open URL):
Type: U (URI)
Payload: https://example.com/product/123Text Record:
Type: T (Text)
Payload: "Tap to connect to Wi-Fi"Smart Poster:
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'background': '#ffffff', 'mainBkg': '#2C3E50', 'secondBkg': '#16A085', 'tertiaryBkg': '#E67E22'}}}%%
flowchart LR
SP[Smart Poster<br/>NDEF Message]
SP --> URL[URL Record<br/>https://movie.com/trailer]
SP --> TEXT[Text Record<br/>Coming Soon: Movie Title]
SP --> MIME[MIME Record<br/>image/png poster]
style SP fill:#2C3E50,stroke:#16A085,color:#fff
style URL fill:#16A085,stroke:#2C3E50,color:#fff
style TEXT fill:#16A085,stroke:#2C3E50,color:#fff
style MIME fill:#E67E22,stroke:#2C3E50,color:#fff
Wi-Fi Configuration (Android):
Type: application/vnd.wfa.wsc
Payload: [Wi-Fi credentials encrypted]877.10 Summary
This chapter covered NFC fundamentals:
- Technical Foundation: NFC operates at 13.56 MHz (HF RFID subset) with 4-10 cm range
- Three Operating Modes: Peer-to-peer, Read/Write, and Card Emulation
- NDEF Standard: Provides interoperable message structure for URLs, text, and custom data
- Tag Types: Five tag types with varying memory, speed, and security capabilities
877.11 What’s Next
Continue to NFC Implementation and Applications to learn hands-on tag programming and explore real-world NFC applications in payments, smart homes, and authentication.
