%% fig-alt: "Cloud IoT security architecture showing three-layer defense"
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'fontSize': '14px'}}}%%
graph TB
subgraph Device[IoT Device Layer]
D1[Device Authentication]
D2[Secure Boot]
D3[Data Encryption]
end
subgraph Network[Network Layer]
N1[TLS/SSL]
N2[VPN Tunnels]
N3[Firewall]
end
subgraph Cloud[Cloud Layer]
C1[Identity & Access Management]
C2[Encryption at Rest]
C3[Security Monitoring]
end
Device -->|Encrypted Data| Network
Network -->|Secure Channel| Cloud
style Device fill:#2C3E50,stroke:#16A085,color:#fff
style Network fill:#16A085,stroke:#2C3E50,color:#fff
style Cloud fill:#E67E22,stroke:#16A085,color:#fff
273 Cloud Security for IoT
273.1 Learning Objectives
By the end of this chapter, you will be able to:
- Implement IAM: Configure identity and access management for IoT cloud systems
- Apply Shared Responsibility: Understand what you secure vs. what the provider secures
- Secure Device Credentials: Implement per-device certificates and avoid credential pitfalls
- Design Multi-Region Security: Apply security patterns for distributed IoT deployments
273.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Cloud Computing Fundamentals: Understanding of NIST cloud model
- Cloud Deployment Models: Knowledge of public, private, and hybrid clouds
- Security and Privacy Overview: Basic security concepts
273.3 Security Overview
Security is paramount in IoT-cloud systems due to the volume and sensitivity of data.
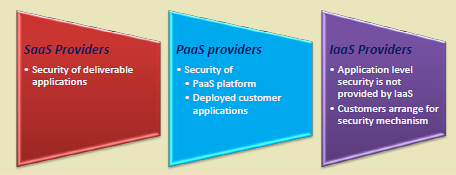
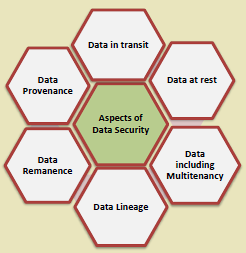
273.4 Pitfall: Hardcoding Cloud Credentials
The Mistake: Embedding AWS access keys, Azure connection strings, or API tokens directly in device firmware that gets flashed to thousands of IoT devices. When one device is compromised or reverse-engineered, attackers gain access to your entire cloud infrastructure.
Why It Happens: Developers test with hardcoded credentials during prototyping and forget to implement proper credential management before production. The firmware build process makes it easy to embed secrets. Certificate-based authentication seems complex compared to a simple API key.
The Fix: Use X.509 certificates with unique per-device identities provisioned during manufacturing. Implement secure boot and hardware security modules (HSM) or trusted platform modules (TPM) where budget allows. At minimum, use device-specific credentials that can be individually revoked if compromised. Cloud platforms provide device provisioning services (AWS IoT Device Defender, Azure DPS) specifically for this purpose.
273.5 Identity and Access Management (IAM)
Core Principles:
- Authentication: Verify identity (who you are)
- Authorization: Grant permissions (what you can do)
- Accounting: Track actions (what you did)
273.7 Multi-Region Deployment Patterns
Deploying IoT systems across multiple geographic regions is essential for global applications requiring low latency, high availability, and regulatory compliance.
273.7.1 Why Multi-Region for IoT?
Latency Requirements: - IoT devices in Asia connecting to US-East data center: 200-400ms - Same devices connecting to Asia-Pacific region: 20-50ms - For real-time control, this difference matters
Regulatory Compliance: - GDPR requires EU data to stay in EU - China’s Cybersecurity Law requires data localization - Healthcare regulations may require specific jurisdictions
273.7.2 Multi-Region Architecture Pattern
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart LR
subgraph US["Region US-East-1 (Primary)"]
US_IOT["IoT Core"]
US_ALB["Application Load Balancer"]
US_RDS["RDS Multi-AZ"]
US_S3["S3 (CRR enabled)"]
end
subgraph EU["Region EU-West-1 (Secondary)"]
EU_IOT["IoT Core"]
EU_ALB["Application Load Balancer"]
EU_RDS["RDS Multi-AZ"]
EU_S3["S3 (Cross-Region Replication)"]
end
US_S3 -->|"Cross-Region Replication"| EU_S3
style US fill:#16A085,stroke:#16A085
style EU fill:#E67E22,stroke:#16A085
273.7.3 Security Considerations for Multi-Region
| Aspect | Single Region | Multi-Region |
|---|---|---|
| Data Sovereignty | Single jurisdiction | Must comply with each region’s laws |
| Key Management | One KMS | Regional KMS instances |
| IAM Policies | Global | May need regional customization |
| Audit Logs | Centralized | Must aggregate from all regions |
| Incident Response | One team timezone | 24/7 coverage needed |
273.7.4 Data Replication Security
- Encryption in Transit: All cross-region replication uses TLS 1.2+
- Encryption at Rest: Each region encrypts with its own KMS key
- Access Control: IAM policies must be consistent across regions
- Audit Trails: CloudTrail logs from all regions sent to central S3
273.8 Cloud Security Best Practices
| Security Layer | Development Approach | Production Requirement |
|---|---|---|
| Authentication | API keys in code | IAM roles, temporary credentials, HSM |
| Encryption | Optional | Required: TLS 1.2+ in-transit, AES-256 at-rest |
| Network | Default VPC | Private subnets, NAT gateway, VPC endpoints |
| Secrets | Hardcoded passwords | AWS Secrets Manager with rotation |
| Compliance | Not audited | SOC 2, ISO 27001, GDPR, HIPAA certifications |
| Access Control | Admin access for everyone | Least-privilege IAM, MFA, audit logs |
| Monitoring | Basic logs | GuardDuty, Security Hub, CloudTrail, Config |
273.9 Incident Response Plan
- Detection: Automated alerts (GuardDuty, CloudWatch)
- Triage: On-call engineer investigates severity (5 min)
- Communication: Update status page, notify stakeholders (15 min)
- Mitigation: Apply fix or rollback (30 min)
- Recovery: Verify service health (1 hour)
- Post-mortem: Document root cause, preventive measures (1 week)
273.10 IAM Knowledge Check
273.11 Common Security Pitfalls
The Mistake: Leaving S3 buckets with public read access or overly permissive bucket policies.
Real Impact: Data breach leading to $500K+ fines under GDPR.
The Fix: - Enable S3 Block Public Access (account-level) - Use AWS Config rules to alert on public buckets - Implement Security Hub continuous compliance monitoring - Regular penetration testing
The Mistake: Granting * (all) permissions to IoT devices or applications for convenience.
Example: "Action": "dynamodb:*" instead of "Action": ["dynamodb:PutItem", "dynamodb:GetItem"]
The Fix: - Apply principle of least privilege - Use IAM Access Analyzer to identify overly permissive policies - Create specific policies for each device type/function - Regular IAM audit reviews
273.12 Summary
This chapter covered cloud security for IoT:
- Multi-Layer Defense: Device, network, and cloud layers each provide security controls
- Per-Device Credentials: X.509 certificates with individual revocation are essential at scale
- Shared Responsibility: Understand what you secure vs. what the provider secures
- Multi-Region Security: Additional complexity requires consistent policies and centralized audit
- Incident Response: Plan and practice before incidents occur
273.13 What’s Next?
Now that you understand cloud security, continue with:
- Cloud Platforms and Message Queues - Compare AWS, Azure, and messaging technologies
- Production Cloud Deployment - Learn about production deployment, cost optimization, and labs
