%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '13px'}}}%%
graph TB
subgraph Pub["Publishers"]
P1[Sensor 1<br/>Temperature]
P2[Sensor 2<br/>Humidity]
P3[Sensor 3<br/>Motion]
end
BROKER[MQTT Broker<br/>Message Router]
subgraph Sub["Subscribers"]
S1[Dashboard App]
S2[Alert Service]
S3[Data Logger]
end
P1 -->|PUBLISH<br/>temp/sensor1| BROKER
P2 -->|PUBLISH<br/>humid/sensor2| BROKER
P3 -->|PUBLISH<br/>motion/sensor3| BROKER
BROKER -->|SUBSCRIBE<br/>temp/#| S1
BROKER -->|SUBSCRIBE<br/>motion/#| S2
BROKER -->|SUBSCRIBE<br/>#| S3
style BROKER fill:#2C3E50,stroke:#16A085,color:#fff
style P1 fill:#16A085,stroke:#0e6655,color:#fff
style P2 fill:#16A085,stroke:#0e6655,color:#fff
style P3 fill:#16A085,stroke:#0e6655,color:#fff
style S1 fill:#E67E22,stroke:#d35400,color:#fff
style S2 fill:#E67E22,stroke:#d35400,color:#fff
style S3 fill:#E67E22,stroke:#d35400,color:#fff
1472 IoT Protocol Security
1472.1 Learning Objectives
By the end of this chapter, you will be able to:
- Secure MQTT Communications: Implement TLS encryption, authentication, and topic-level access control for MQTT brokers
- Understand MQTT Vulnerabilities: Identify and mitigate UTF-8 validation DoS attacks and QoS abuse
- Secure CoAP Endpoints: Apply DTLS encryption and rate limiting for constrained devices
- Prevent Amplification Attacks: Understand and mitigate CoAP amplification vulnerabilities
- Compare Protocol Security: Select appropriate security measures based on protocol characteristics
What is IoT Protocol Security? IoT devices communicate using specialized protocols designed for constrained environments. MQTT (Message Queuing Telemetry Transport) uses a publish-subscribe pattern where devices send messages through a central broker. CoAP (Constrained Application Protocol) provides REST-like communication over UDP for resource-limited devices. Both protocols require specific security measures beyond standard web security.
Why does it matter? In 2022, security researchers found that 47% of publicly exposed MQTT brokers had no authentication—anyone could connect and control devices. Unsecured IoT protocols enable attackers to intercept sensor data, send malicious commands to actuators, or use devices as DDoS amplifiers.
Key terms: | Term | Definition | |——|————| | MQTT | Message Queuing Telemetry Transport—lightweight pub/sub messaging protocol for IoT | | CoAP | Constrained Application Protocol—UDP-based REST protocol for constrained devices | | DTLS | Datagram TLS—security protocol for UDP-based communications | | QoS | Quality of Service—message delivery guarantees (0: at-most-once, 1: at-least-once, 2: exactly-once) | | Topic ACL | Access Control List defining which clients can publish/subscribe to which topics |
1472.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Software Vulnerabilities and Web Security: Understanding of common attack patterns and defense-in-depth
- Networking Fundamentals: Understanding of TCP/UDP and network protocols
- Application Protocols: Basic knowledge of MQTT and CoAP operation
- Encryption Principles: Understanding of TLS and encryption concepts
1472.3 MQTT (Message Queuing Telemetry Transport)
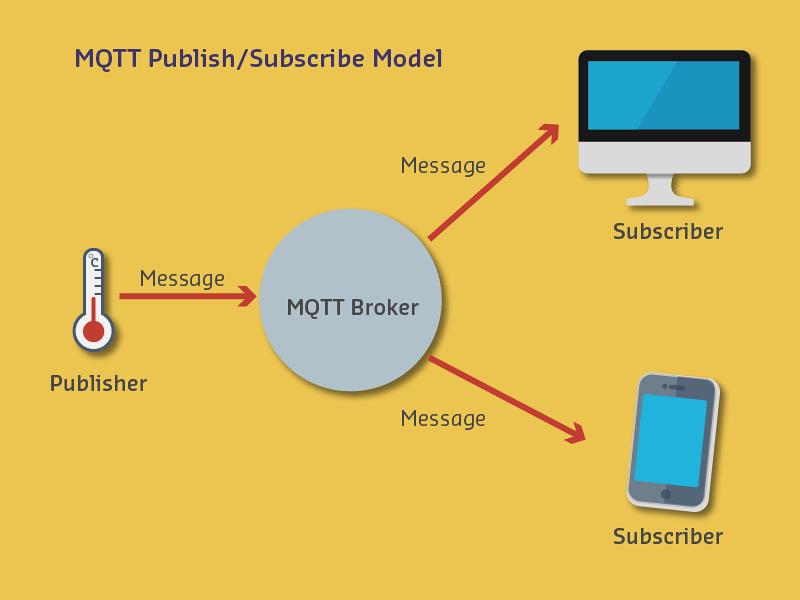
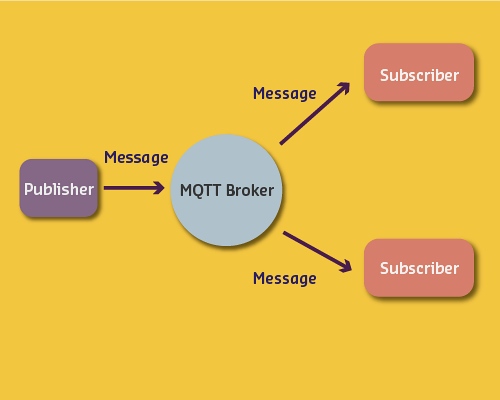
Architecture: Publish-Subscribe pattern with message broker.
Topic Hierarchy: adt/lora/adeunis/0018B2000000023A - Hierarchical organization with / separators - Wildcard subscriptions: # (multi-level), + (single-level)
1472.3.1 MQTT Security Risks
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '12px'}}}%%
flowchart TD
A[Malicious Client<br/>Sends Invalid UTF-8] --> B{Broker<br/>Validates?}
B -->|No| C[Broker Forwards<br/>Invalid Message]
B -->|Yes| D[Broker Rejects<br/>Attack Stopped]
C --> E[Subscriber Validates<br/>Detects Invalid UTF-8]
E --> F[Subscriber Disconnects<br/>Rejects Message]
F --> G[Broker Retries QoS=2<br/>Guaranteed Delivery]
G --> E
G --> H[Denial of Service<br/>Infinite Retry Loop]
style A fill:#e74c3c,stroke:#c0392b,color:#fff
style B fill:#E67E22,stroke:#d35400,color:#fff
style C fill:#e74c3c,stroke:#c0392b,color:#fff
style D fill:#16A085,stroke:#0e6655,color:#fff
style E fill:#E67E22,stroke:#d35400,color:#fff
style F fill:#e74c3c,stroke:#c0392b,color:#fff
style G fill:#e74c3c,stroke:#c0392b,color:#fff
style H fill:#e74c3c,stroke:#c0392b,color:#fff
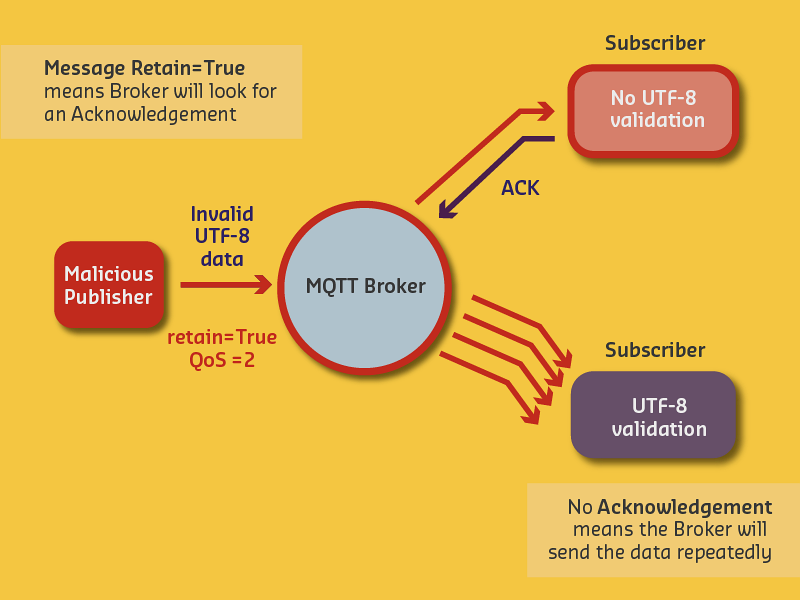
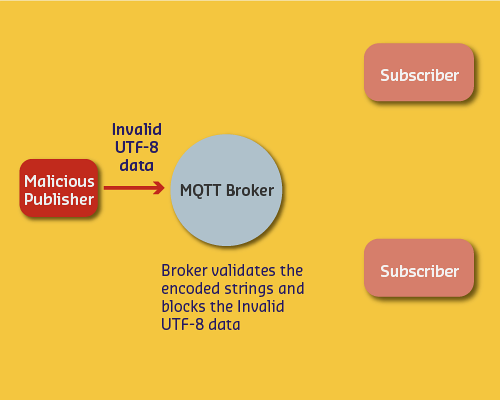
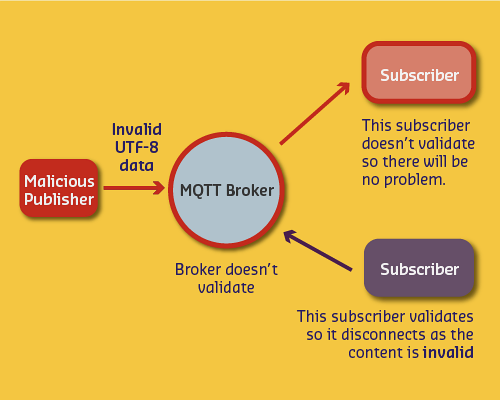
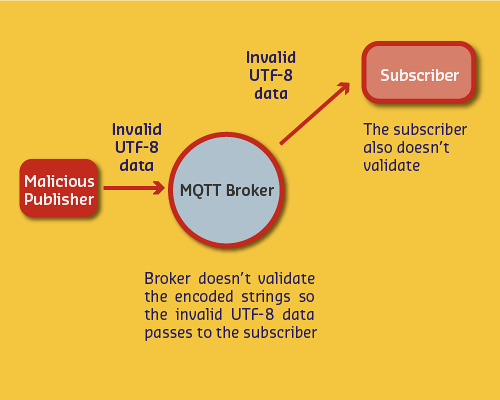
UTF-8 Validation DoS Attack:
- Malicious client sends invalid UTF-8 characters
- Broker doesn’t validate (passes through)
- Subscriber validates and disconnects
- Broker retries delivery (QoS=2)
- Continuous retry = Denial of Service
Mitigation: - Always validate UTF-8 at broker - Disable QoS=2 if not needed - Implement rate limiting
1472.3.2 MQTT Security Implementation
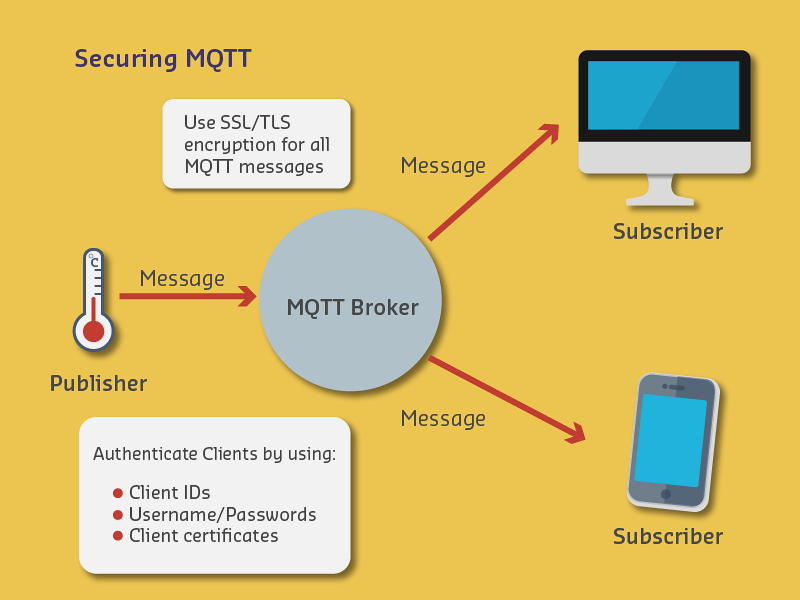
Secure MQTT implementations require TLS encryption, authentication, topic-level access control, and UTF-8 validation. Production systems should use libraries like paho-mqtt with proper certificate management and QoS configuration.
1472.3.3 MQTT Security Configuration Checklist
| Security Control | Implementation | Notes |
|---|---|---|
| Transport Encryption | TLS 1.3 on port 8883 | Disable TLS 1.0/1.1 |
| Authentication | Username/password or X.509 certificates | No anonymous connections |
| Authorization | Topic-level ACLs | Restrict pub/sub per client |
| Message Validation | UTF-8 validation at broker | Prevent encoding attacks |
| Rate Limiting | Message rate limits per client | Prevent flooding |
| Last Will Testament | Configure for ungraceful disconnection | Detect compromised clients |
1472.4 CoAP (Constrained Application Protocol)
Characteristics: - UDP-based (smaller packets than MQTT) - No central broker required - RESTful API (GET, POST, PUT, DELETE) - Multicast support - Resource observation
Security: DTLS (Datagram TLS) for CoAP = CoAPs
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '13px'}}}%%
graph LR
subgraph CoAP["CoAP Protocol Stack"]
APP[Application<br/>GET/POST/PUT/DELETE]
COAP[CoAP Layer<br/>RESTful Requests]
UDP[UDP Transport<br/>Lightweight]
end
subgraph CoAPS["CoAPS (Secure)"]
APPS[Application<br/>GET/POST/PUT/DELETE]
COAPS[CoAP Layer<br/>RESTful Requests]
DTLS[DTLS Security<br/>Encryption + Auth]
UDPS[UDP Transport<br/>Lightweight]
end
CoAP -.->|Add Security| CoAPS
style APP fill:#2C3E50,stroke:#16A085,color:#fff
style COAP fill:#E67E22,stroke:#d35400,color:#fff
style UDP fill:#16A085,stroke:#0e6655,color:#fff
style APPS fill:#2C3E50,stroke:#16A085,color:#fff
style COAPS fill:#E67E22,stroke:#d35400,color:#fff
style DTLS fill:#16A085,stroke:#0e6655,color:#fff
style UDPS fill:#16A085,stroke:#0e6655,color:#fff
Vulnerabilities: - IP address spoofing (IPv4) - Amplification attacks (small request triggers large response) - Amplification factor: 10-50x
The Misconception: If I use HTTPS, my IoT data is fully protected.
Why It’s Wrong: - HTTPS only protects data IN TRANSIT (network) - Data at rest (storage) needs separate encryption - Data in use (memory) can be extracted - Endpoints may be compromised (device or server) - Metadata (who talks to whom) still visible
Real-World Example: - Smart thermostat sends data over HTTPS - Data encrypted during transmission - Data stored in cloud database: Unencrypted! - Database breach: All temperature history exposed - HTTPS didn’t protect the stored data
The Correct Understanding: | Data State | HTTPS Protection | Additional Needed | |————|——————|——————-| | In transit | Protected | - | | At rest (storage) | Not protected | Database encryption, KMS | | In use (memory) | Not protected | Secure enclaves (TEE) | | Metadata | Not protected | VPN, anonymization |
HTTPS is necessary but not sufficient. Encrypt data at every state: transit, rest, and use.
1472.5 IoT Protocol Security Comparison
This view compares security features across major IoT application protocols, helping select the right protocol for your security requirements:
%% fig-alt: "IoT protocol security comparison showing MQTT, CoAP, and HTTP(S) across five security dimensions: encryption support where all support TLS/DTLS but with different overhead, authentication methods ranging from username/password to certificates to OAuth, authorization granularity from topic-level ACLs to URI-based permissions, resource constraints showing MQTT and CoAP optimized for constrained devices while HTTP higher overhead, and attack surface showing MQTT vulnerable to broker compromise, CoAP to amplification, HTTP to standard web attacks. Decision guide included for protocol selection based on use case."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart TB
subgraph COMPARE["IoT PROTOCOL SECURITY COMPARISON"]
subgraph MQTT_SEC["MQTT"]
M1["Encryption: TLS 1.2/1.3<br/>Port 8883"]
M2["Auth: Username/Password<br/>or X.509 Certificates"]
M3["Authz: Topic-level ACLs<br/>Wildcard patterns"]
M4["Overhead: Low<br/>2-byte header"]
M5["Risk: Broker is SPF<br/>All traffic routes through"]
end
subgraph COAP_SEC["CoAP"]
C1["Encryption: DTLS 1.2<br/>UDP-based"]
C2["Auth: Pre-shared Keys<br/>or Certificates"]
C3["Authz: URI permissions<br/>Resource-level"]
C4["Overhead: Very Low<br/>4-byte header"]
C5["Risk: Amplification<br/>10-50x factor"]
end
subgraph HTTP_SEC["HTTP/REST"]
H1["Encryption: TLS 1.2/1.3<br/>HTTPS standard"]
H2["Auth: OAuth 2.0<br/>API keys, JWT"]
H3["Authz: Endpoint ACLs<br/>Fine-grained"]
H4["Overhead: High<br/>~200 byte headers"]
H5["Risk: Web vulnerabilities<br/>XSS, CSRF, SQLi"]
end
end
DECISION["SELECT PROTOCOL"] --> Q1{Constrained<br/>Device?}
Q1 -->|Yes| Q2{Real-time<br/>Needed?}
Q1 -->|No| HTTP_SEC
Q2 -->|Yes| MQTT_SEC
Q2 -->|No| COAP_SEC
style M1 fill:#2C3E50,stroke:#16A085,color:#fff
style M2 fill:#16A085,stroke:#0e6655,color:#fff
style M3 fill:#16A085,stroke:#0e6655,color:#fff
style M4 fill:#16A085,stroke:#0e6655,color:#fff
style M5 fill:#E67E22,stroke:#d35400,color:#fff
style C1 fill:#2C3E50,stroke:#16A085,color:#fff
style C2 fill:#16A085,stroke:#0e6655,color:#fff
style C3 fill:#16A085,stroke:#0e6655,color:#fff
style C4 fill:#16A085,stroke:#0e6655,color:#fff
style C5 fill:#E67E22,stroke:#d35400,color:#fff
style H1 fill:#2C3E50,stroke:#16A085,color:#fff
style H2 fill:#16A085,stroke:#0e6655,color:#fff
style H3 fill:#16A085,stroke:#0e6655,color:#fff
style H4 fill:#E67E22,stroke:#d35400,color:#fff
style H5 fill:#E67E22,stroke:#d35400,color:#fff
style DECISION fill:#2C3E50,stroke:#16A085,color:#fff
style Q1 fill:#E67E22,stroke:#d35400,color:#fff
style Q2 fill:#E67E22,stroke:#d35400,color:#fff
Protocol Selection Guide: - MQTT: Best for pub/sub patterns, many devices, real-time data (smart home, industrial sensors) - CoAP: Best for request/response with constrained devices (battery-powered sensors, LPWAN) - HTTP/REST: Best for cloud integration, web apps, non-constrained gateways
1472.6 Knowledge Check
Question 1: An MQTT broker is configured with no authentication. What’s the MOST critical security risk?
No authentication = complete unauthorized access! Attacker capabilities: 1) Subscribe to ANY topic: home/+/password, hospital/patient/+/vitals (steal data), 2) Publish to ANY topic: smart_lock/unlock (open doors), thermostat/set_temp (physical damage), 3) Enumerate topics: Discover system architecture, 4) DoS: Flood broker with messages. Proper security layers: 1) Authentication: Username/password or certificates, 2) Authorization/ACL: Topic-level permissions, 3) Encryption: TLS 1.3. Encryption alone (option C) protects confidentiality but doesn’t prevent unauthorized access!
Question 2: Which QoS level can amplify MQTT UTF-8 validation DoS attacks?
QoS 2 guarantees delivery through a four-way handshake, causing the broker to retry indefinitely if the subscriber rejects invalid UTF-8 messages. This creates an infinite retry loop. Mitigation: Validate UTF-8 at the broker level, use QoS 0 or 1 when guaranteed delivery isn’t critical.
Question 3: What security protocol does CoAP use?
DTLS (Datagram Transport Layer Security) provides TLS-like security for UDP-based protocols like CoAP. Since CoAP runs over UDP (connectionless), it cannot use standard TLS which requires TCP. DTLS adapts TLS for datagram transport, providing encryption, authentication, and integrity for CoAP communications.
Question 4: Which attack exploits CoAP’s UDP-based design?
Amplification attacks exploit CoAP’s UDP-based design. Attackers send small requests with spoofed source IP addresses that trigger large responses directed at the victim. CoAP’s amplification factor can reach 10-50x. Mitigation: Rate limiting, response caching, DTLS authentication (prevents source IP spoofing).
Question 5: MQTT QoS 2 uses a four-way handshake (PUBLISH, PUBREC, PUBREL, PUBCOMP). When is this overhead justified for IoT?
QoS 2 is for critical, non-idempotent operations where duplicates cause harm! QoS 0: Fire-and-forget, for frequent sensor readings. QoS 1: May duplicate, for alerts and logs. QoS 2: Guaranteed single delivery, for financial transactions, door unlock commands, billing events. QoS 2 overhead: 4 messages vs 1, higher latency, more bandwidth—use sparingly!
1472.7 Summary
This chapter covered IoT protocol security for MQTT and CoAP:
MQTT Security: - Publish-subscribe architecture with central broker - Requires TLS encryption (port 8883), authentication, and topic ACLs - UTF-8 validation DoS attack mitigated by broker-side validation - QoS levels: Use QoS 2 only for critical non-idempotent operations
CoAP Security: - UDP-based REST protocol for constrained devices - DTLS provides encryption and authentication - Vulnerable to amplification attacks (10-50x factor) - Rate limiting and response caching for mitigation
Protocol Selection: - MQTT: Real-time pub/sub with many devices - CoAP: Request/response for constrained devices - HTTP: Cloud integration with non-constrained gateways
1472.8 What’s Next
Continue to Authentication and Credentials to learn about password security, multi-factor authentication, and credential management for IoT systems.
