%%{init: {'theme': 'base', 'themeVariables': {'primaryColor':'#2C3E50','primaryTextColor':'#fff','primaryBorderColor':'#16A085','lineColor':'#16A085','secondaryColor':'#E67E22','tertiaryColor':'#7F8C8D','fontSize':'16px'}}}%%
graph TB
A[RFID Attack Vectors] --> B[Eavesdropping]
A --> C[Cloning/Replay]
A --> D[Man-in-the-Middle]
A --> E[Denial of Service]
A --> F[Physical Attacks]
A --> G[Privacy Violations]
B --> B1["Passive listening<br/>Range can exceed intended reads<br/>(cm–tens of meters)"]
B --> B2["No authentication<br/>Static IDs broadcast"]
C --> C1["Copy tag UID<br/>Clone access card"]
C --> C2["Replay captured data<br/>Commodity tools exist"]
D --> D1["Ghost-and-Leech<br/>Relay attack extension"]
D --> D2["Modify data in transit<br/>Payment manipulation"]
E --> E1["RF jamming<br/>Block communication"]
E --> E2["Kill command abuse<br/>Permanent disable"]
F --> F1["Invasive probing<br/>Extract crypto keys"]
F --> F2["Side-channel analysis<br/>Power/timing leaks"]
G --> G1["Track individuals<br/>Unique tag IDs"]
G --> G2["Build behavior profiles<br/>Retail surveillance"]
style A fill:#2C3E50,stroke:#16A085,color:#fff
style B fill:#E67E22,stroke:#2C3E50,color:#fff
style C fill:#E67E22,stroke:#2C3E50,color:#fff
style D fill:#E67E22,stroke:#2C3E50,color:#fff
style E fill:#E67E22,stroke:#2C3E50,color:#fff
style F fill:#E67E22,stroke:#2C3E50,color:#fff
style G fill:#E67E22,stroke:#2C3E50,color:#fff
870 RFID Security and Privacy
870.1 Learning Objectives
By the end of this chapter, you will be able to:
- Identify RFID Vulnerabilities: Analyze eavesdropping, cloning, tracking, and replay attack vectors
- Compare Tag Security Levels: Evaluate passive, semi-active, and active tag security capabilities
- Implement RFID Security Controls: Apply encryption, mutual authentication, and kill commands
- Understand Privacy Threats: Assess tracking risks from RFID-enabled items and supply chains
- Design Privacy-Preserving Systems: Implement blocker tags, Faraday cages, and privacy-aware protocols
- Apply Regulatory Compliance: Navigate GDPR, CCPA, and industry-specific RFID privacy requirements
870.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- RFID Fundamentals and Standards: Understanding RFID technology, frequency bands, tag types, and ISO standards provides the foundation for evaluating security vulnerabilities specific to different RFID implementations
- RFID Hands-on and Applications: Practical experience with RFID systems and real-world applications helps contextualize the security risks and countermeasures discussed in this chapter
- Networking Basics: Knowledge of wireless security concepts (encryption, authentication, access control) is essential for understanding RFID-specific security mechanisms
- Basic cryptography concepts: Familiarity with encryption algorithms (AES), authentication protocols, and key management helps understand advanced RFID security features like mutual authentication and secure elements
Deep Dives: - RFID Fundamentals and Standards - Core RFID technology concepts - RFID Hands-on and Applications - Practical RFID implementations - RFID Architecture - Tag types and system design
Comparisons: - NFC Security - Security in NFC (HF RFID subset) - NFC vs RFID - When to use which technology - Bluetooth Security - Alternative wireless security
Related Technologies: - NFC Fundamentals - High-frequency RFID subset - 6LoWPAN Security - IPv6 network security - Zigbee Security - Mesh network security
Security & Privacy: - IoT Security Overview - Broader security context - Privacy Introduction - Privacy frameworks and GDPR - Threats and Vulnerabilities - Attack vectors - Encryption Architecture - Cryptographic protection
Products:
Learning: - Quizzes Hub - Test RFID security knowledge - RFID Comprehensive Review - Complete RFID overview
RFID security is about protecting the radio communication between tags and readers from attackers. Since RFID uses radio waves, anyone with the right equipment can potentially intercept, copy, or manipulate these signals.
The Three Main Threats:
| Threat | What Happens | Real-World Example |
|---|---|---|
| Eavesdropping | Attacker secretly listens to RFID communication | Skimming a contactless card’s response at close range |
| Cloning | Attacker copies your tag to make a duplicate | Copying building access card to gain unauthorized entry |
| Tracking | Attacker follows your movements via RFID | Retail stores tracking which products you carry |
Why Basic RFID Tags Are Vulnerable:
Most cheap RFID tags (like inventory labels) have no security at all. They simply broadcast their ID number whenever a reader asks. It’s like having a name tag that anyone can read from across the room.
The Good News:
More secure tags exist (like those in modern credit cards and passports) that use encryption and require the reader to prove its identity before responding. However, these cost more and require proper implementation.
Simple Analogy:
| Tag Type | Security Level | Analogy |
|---|---|---|
| Basic passive tag | None | Shouting your name when anyone asks |
| Password-protected tag | Low | Only responding to correct password |
| Encrypted tag (DESFire) | High | Speaking in secret code only you and trusted people understand |
| Mutual authentication | Very High | Both sides prove identity before talking |
Bottom Line: If security matters (payments, access control, identity), use encrypted tags with authentication. For basic inventory tracking, simple tags are usually fine.
Scenario: You’re securing a pharmaceutical warehouse. Pallets are tagged with UHF RFID for automated inventory tracking. You’re concerned about (1) unauthorized inventory reads from outside the facility and (2) cloning/tampering that could let counterfeit pallets enter the workflow. The security upgrade must fit within a constrained budget and maintenance capacity.
Think about: 1. What security properties do you need from the tag (authenticated reads, anti-cloning, tamper evidence, privacy)? 2. What facility-level controls help (read-zone design, physical barriers/shielding, reader access control, monitoring)?
Key Insight: Prefer defense-in-depth: - Use UHF tags/readers that support authenticated reads (e.g., EPC Gen2v2 features) when your threat model includes cloning or unauthorized reads. - Engineer the RF environment: limit read zones with antenna placement and power tuning, and consider shielding where necessary (validated by a site survey). - Treat key management and backend controls as first‑class: protect reader credentials, rotate keys, log reads, and reconcile anomalies.
Verify Your Understanding: - Why can authenticated tags still benefit from read-zone control or shielding? - What operational processes (key provisioning/rotation, reader authorization) matter as much as tag choice?
870.3 RFID Attack Vectors
Understanding how RFID systems can be attacked is essential for designing secure implementations. RFID vulnerabilities stem from wireless communication, limited computational power in passive tags, and the need for interoperability across different systems.
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
quadrantChart
title RFID Security Countermeasures: Cost vs Protection Level
x-axis Low Cost --> High Cost
y-axis Basic Protection --> Strong Protection
quadrant-1 Recommended for High-Value
quadrant-2 Best Balance
quadrant-3 Basic Deterrent
quadrant-4 Over-Engineered
Faraday Sleeve: [0.15, 0.45]
Kill Command: [0.25, 0.35]
Blocker Tag: [0.30, 0.50]
Password Auth: [0.35, 0.55]
AES Encryption: [0.55, 0.80]
Mutual Auth: [0.65, 0.85]
Challenge-Response: [0.70, 0.90]
Secure Element: [0.85, 0.95]
Figure takeaway: RFID attacks range from passive eavesdropping and cloning to relay/DoS and physical key-extraction; the practical range and cost vary significantly by frequency band and tag type.
870.3.1 Eavesdropping
RFID communication is broadcast over radio waves, making it susceptible to interception by unauthorized parties. The effective eavesdropping range typically exceeds the intended read range:
| Frequency Band | Intended Read Range | Potential Interception Range | Notes |
|---|---|---|---|
| LF (125 kHz) | cm-scale | cm-scale | Near-field magnetic coupling; interception typically requires close proximity and tuned coils |
| HF (13.56 MHz) | cm-scale | cm to meters | Still near-field; range depends on antennas, shielding, and environment |
| UHF (860-960 MHz) | meters | meters to beyond the intended zone | Far-field; directional antennas and placement can significantly increase range |
Vulnerability: Passive tags have no built-in encryption. The tag ID and any data stored on the tag are transmitted in plaintext. An attacker with a sensitive receiver positioned between the reader and tag can intercept all communication.
Real-World Example: Researchers have shown that some contactless cards can be skimmed at close range with commodity NFC/SDR equipment. Modern EMV systems reduce what an attacker can do with the data (dynamic cryptograms), but privacy exposure and relay risk can still matter.
870.3.2 Cloning and Replay Attacks
Once an attacker captures RFID data through eavesdropping, they can create counterfeit tags or replay captured authentication sequences.
Cloning Process: 1. Capture: Use eavesdropping to record tag UID and data 2. Copy: Write captured data to blank writable tag (e.g., EM4305, NTAG216) 3. Impersonate: Present cloned tag to readers as if it were the original
Practical note: Cloning insecure LF/HF tags can be done with commodity tooling and writable tags. The barrier is low for systems that rely on static identifiers or broken cryptography.
Real-World Impact: - Building Access Control: Clone employee badge to gain unauthorized entry - Transportation: Copy transit cards for free rides (early MIFARE Classic vulnerability) - Livestock Tracking: Clone animal RFID tags to misrepresent pedigree/ownership
870.3.3 Man-in-the-Middle (MITM) Attacks
RFID MITM attacks involve inserting an attacker’s device between the legitimate reader and tag, intercepting and potentially modifying communication in real-time.
Ghost-and-Leech Attack: - Ghost: Attacker’s device near victim’s tag (relays to Leech) - Leech: Attacker’s device near legitimate reader (relays to Ghost) - Effect: Extends read range well beyond the intended proximity (research prototypes have demonstrated large extensions under controlled conditions)
Example Scenario: Attacker positions Ghost device next to victim’s contactless payment card in subway. Leech device near payment terminal. Relay happens wirelessly, enabling payment from victim’s card without physical proximity.
Defense Challenge: Even encrypted tags vulnerable to relay attacks because attacker isn’t breaking encryption—just relaying encrypted messages in real-time.
870.3.4 Denial of Service (DoS)
RFID systems can be disrupted through RF jamming or abuse of tag management commands.
RF Jamming: - Method: Transmit noise on RFID frequency band - Effect: Prevents legitimate reader-tag communication - Barrier: From simple interference sources to purpose-built transmitters; practicality depends on proximity and power limits - Detection: Difficult to distinguish from environmental RF interference
Kill Command Abuse: - Purpose: EPC Gen 2 tags support permanent deactivation (“kill” command) to address privacy concerns - Vulnerability: If attacker learns kill password (often factory default), can permanently disable tags - Impact: Supply chain disruption, inventory tracking failure
Example: Researchers have shown that tags using default/weak kill passwords can be disabled at scale, disrupting inventory workflows.
870.3.5 Physical Attacks
Physical access to RFID tags enables invasive attacks to extract cryptographic keys or bypass security measures.
Invasive Probing: - Method: De-capsulate chip, use microprobes to access internal circuits - Target: Extract secret keys from secure element - Barrier: Requires specialized lab equipment and expertise (high effort and cost) - Timeframe: Days to weeks for skilled attacker
Side-Channel Analysis: - Power Analysis: Measure chip power consumption during crypto operations to deduce key bits - Timing Analysis: Measure operation duration variations to infer secret data - Electromagnetic Analysis: Monitor EM emissions during computation
Real-World Note: Researchers extracted MIFARE Classic crypto keys using side-channel techniques, which enabled cloning in some deployments and drove migration to more secure cards.
870.4 Privacy Threats
RFID enables covert tracking and surveillance due to unique tag identifiers and long read ranges.
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor':'#2C3E50','primaryTextColor':'#fff','primaryBorderColor':'#16A085','lineColor':'#16A085','secondaryColor':'#E67E22','tertiaryColor':'#7F8C8D','fontSize':'16px'}}}%%
graph LR
A[RFID Privacy Threats] --> B[Individual Tracking]
A --> C[Behavioral Profiling]
A --> D[Data Aggregation]
B --> B1["Unique tag IDs<br/>Persistent identity"]
B --> B2["Movement tracking<br/>Readers at choke points"]
B --> B3["Association attacks<br/>Link person to items"]
C --> C1["Retail analytics<br/>Shopping patterns"]
C --> C2["Workplace surveillance<br/>Badge tracking"]
C --> C3["Social graph inference<br/>Co-location data"]
D --> D1["Cross-database linking<br/>Purchase + location"]
D --> D2["De-anonymization<br/>Re-identify individuals"]
D --> D3["Third-party sharing<br/>Data brokers"]
style A fill:#2C3E50,stroke:#16A085,color:#fff
style B fill:#E67E22,stroke:#2C3E50,color:#fff
style C fill:#E67E22,stroke:#2C3E50,color:#fff
style D fill:#E67E22,stroke:#2C3E50,color:#fff
Figure takeaway: Privacy risks come from stable identifiers plus dense reader deployments—enabling tracking, profiling, and cross-database linkage even when tags only reveal “an ID.”
870.4.1 Unique Identifier Tracking
Most RFID tags broadcast a unique identifier (UID or EPC) that remains constant throughout the tag’s lifetime. This enables:
Person-Item Association: - Tags in clothing, products, documents create persistent digital signature - Example: Walk through mall with 5 RFID-tagged items = 5 unique identifiers forming trackable profile
Choke Point Surveillance: - RFID readers at entrances, exits, checkout lanes capture tag IDs - Build timeline of movements: “UID 12345 seen at Store A 2:15pm, Store B 3:05pm, Exit 4:23pm”
Data Retention: - No technical reason to delete historical reads - Enables retroactive tracking: “Who visited both locations X and Y on date Z?”
Quantified Example: Benetton clothing trial (2003) embedded RFID in garments. Privacy advocates calculated that person wearing 3 tagged items could be tracked across 89% of retail locations in test city.
870.4.2 Behavioral Profiling
Aggregated RFID data enables inference of sensitive personal information.
Retail Analytics: - Dwell Time: How long person lingers near products - Path Analysis: Movement patterns through store - Purchase Correlation: Items examined vs. items purchased - Return Visits: Frequency and timing of store visits
Workplace Surveillance: - Employee badge RFID readers at desks, conference rooms, restrooms - Infer: meeting attendance, break duration, co-worker interactions - Correlate with productivity metrics for performance evaluation
Health Inference: - Prescription bottle RFID tags + pharmacy readers - Infer medical conditions from medication patterns - Cross-reference with insurance databases
870.4.3 Data Aggregation and De-anonymization
Combining RFID data with other datasets enables re-identification of “anonymous” data.
Cross-Database Linking:
| Data Source | Information Provided | De-anonymization Risk |
|---|---|---|
| Credit Card | Purchase items, timestamp, store | High (name from payment) |
| RFID Tag IDs | Product list, movement pattern | Medium (needs linkage) |
| Loyalty Card | Purchase history, demographics | High (registered identity) |
| Wi-Fi MAC | Device presence, location history | Medium (device fingerprint) |
Example Attack: Researchers demonstrated linking “anonymous” retail RFID data with credit card transactions by matching timestamps and item sets, achieving 87% re-identification accuracy with just 4 unique purchases.
Third-Party Sharing: - RFID data sold to data brokers - Combined with marketing databases, social media, location data - Creates comprehensive personal profiles without consent
870.5 RFID Security Controls
Implementing security controls requires balancing protection level, cost, and performance.
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor':'#2C3E50','primaryTextColor':'#fff','primaryBorderColor':'#16A085','lineColor':'#16A085','secondaryColor':'#E67E22','tertiaryColor':'#7F8C8D','fontSize':'16px'}}}%%
graph TB
A[RFID Security Controls] --> B[Tag-Level]
A --> C[System-Level]
A --> D[Physical]
B --> B1["Encryption<br/>AES-128, DES"]
B --> B2["Authentication<br/>Challenge-response"]
B --> B3["Kill/Sleep<br/>Deactivation"]
B --> B4["Rolling IDs<br/>Randomized UIDs"]
C --> C1["Reader Authentication<br/>Mutual auth protocols"]
C --> C2["Backend Security<br/>TLS, database encryption"]
C --> C3["Access Control<br/>Role-based permissions"]
C --> C4["Audit Logging<br/>Read tracking"]
D --> D1["Faraday Cages<br/>RF shielding"]
D --> D2["Distance Limiting<br/>Read range reduction"]
D --> D3["Tag Removal<br/>Detachment at sale"]
D --> D4["Blocker Tags<br/>Active jamming"]
style A fill:#2C3E50,stroke:#16A085,color:#fff
style B fill:#16A085,stroke:#2C3E50,color:#fff
style C fill:#16A085,stroke:#2C3E50,color:#fff
style D fill:#16A085,stroke:#2C3E50,color:#fff
Figure takeaway: Effective RFID security is layered—combine tag-level crypto and access control with backend governance (logging, authorization) and physical mitigations (shielding, range limiting).
870.5.1 Encryption and Authentication
Symmetric Encryption: - AES-128: Used in EPC Gen 2v2, NFC Type 4 (DESFire) - 3DES: Legacy encryption in MIFARE DESFire EV1 - Untraceable Authentication: Tag proves possession of key without revealing UID
Challenge-Response Authentication:
Reader → Tag: "Challenge: Random_Number_12345"
Tag → Reader: "Response: Encrypt(Random_Number_12345, Secret_Key)"
Reader: Verify response matches expected encryptionRelative Cost/Complexity (Rule of Thumb):
| Tag Type (Example) | Security Level | Relative Cost | Typical Use Case |
|---|---|---|---|
| Basic EPC Gen 2 | None (static UID) | Low | Retail inventory, non-sensitive |
| Gen 2v2 (AES-128) | Authenticated reads | Medium | High-value items, anti-cloning needs |
| MIFARE DESFire EV3 | AES + secure element | Medium–High | Transit, access control, payments |
| Active tags (encrypted) | Strong crypto + battery | High | Asset tracking with sensors, cold chain |
870.5.2 Mutual Authentication
Prevents rogue readers from interrogating tags by requiring readers to prove their identity.
Protocol Flow: 1. Reader sends authentication request with certificate/credential 2. Tag verifies reader is authorized 3. Tag responds with challenge 4. Reader proves possession of secret key 5. Secure session established
Benefit: Protects against unauthorized reading by competitors or malicious actors.
Implementation: NFC Forum Type 4 tags, EPC Gen 2v2 with backend integration.
870.5.3 Kill and Sleep Commands
Kill Command: - Purpose: Permanently deactivate tag to protect consumer privacy - Mechanism: Irreversible—tag never responds to queries again - Password Protected: 32-bit kill password required - Use Case: Retail point-of-sale deactivation after purchase
Sleep Command: - Purpose: Temporarily disable tag - Mechanism: Tag enters low-power state, ignores queries - Reactivation: Special wake-up signal or password required - Use Case: Transportation logistics (deactivate during transit, reactivate at warehouse)
Vulnerability: Default passwords (often 0x00000000) enable unauthorized kill/sleep.
870.5.4 Rolling and Randomized Identifiers
Problem: Static UIDs enable tracking.
Solution: Tag changes UID each read using pseudorandom algorithm synchronized with authorized readers.
Implementation: - NFC Tag Emulation: Modern smartphones randomize NFC UIDs (Android 10+, iOS 13+) - EPC Gen 2v2: Optional XPC (eXtended Protocol Control) feature supports UID masking - Custom Tags: High-security applications use proprietary rolling-code schemes
Trade-off: Increased complexity, requires backend synchronization, may reduce read reliability.
870.5.5 Physical Security Measures
Faraday Cages and RF Shielding: - Material: Conductive mesh fabric (copper, silver-plated nylon) - Effectiveness: Varies by construction and seams; can dramatically attenuate RF in the targeted band - Applications: RFID-blocking wallets, passports sleeves, server rooms - Cost: Low for small sleeves/wallets; high for room-scale shielding and professional installation
Blocker Tags: - Concept: Emit signals that prevent readers from singulating (identifying) nearby tags - Privacy Enhancement: Simulate presence of many tags, overwhelming reader - Limitation: May interfere with legitimate RFID operations in vicinity - Status: Prototype stage, limited commercial availability
Tag Removal: - Retail: Remove or deactivate tags at point of sale - Consumer Notification: Label items containing RFID tags - Regulation: California SB 1834 (2004) required consumer notification for item-level RFID
870.6 Privacy-Preserving Protocols
Advanced protocols designed to protect privacy while maintaining RFID functionality.
870.6.1 Hash-Based Tag Identifiers
Approach: Tag stores hash of secret key + counter instead of static UID.
Operation: 1. Reader queries tag 2. Tag responds with H(Secret_Key || Counter) 3. Backend database searches hash table for match 4. Counter increments for next read
Privacy Benefit: Different hash each read prevents tracking.
Challenge: Backend must maintain hash table for all possible counter values (computationally expensive for large deployments).
870.6.2 Re-encryption Mixnets
Approach: Encrypt RFID data multiple times, route through mix network of servers that strip one encryption layer each.
Privacy Benefit: No single server sees both tag UID and reader location.
Application: Privacy-preserving supply chain tracking where multiple untrusted parties involved.
Drawback: High latency (multiple server hops), complex infrastructure.
870.7 Regulatory and Compliance
Privacy regulations increasingly cover RFID deployments.
870.7.1 GDPR (General Data Protection Regulation)
Applicability: EU citizens, data processed in EU.
Key Requirements: - Consent: Inform individuals about RFID use - Purpose Limitation: Collect only data necessary for stated purpose - Data Minimization: Shortest retention period - Right to Erasure: Delete personal data on request
RFID Implications: - Static UIDs may constitute “personal data” if linked to individuals - Tracking individuals via RFID requires consent - Retailers must disable/remove item-level tags at sale (unless consumer agrees)
Penalty: Up to €20M or 4% global revenue (whichever greater).
870.7.2 CCPA (California Consumer Privacy Act)
Applicability: California residents, businesses meeting revenue/data thresholds.
RFID-Specific Rights: - Right to Know: What RFID data collected, how used, with whom shared - Right to Delete: Request deletion of RFID-linked data - Right to Opt-Out: Decline sale of data to third parties
Example: California retailer using RFID for inventory must disclose if RFID data combined with loyalty program data to track individuals.
870.7.3 Industry-Specific Regulations
Healthcare (HIPAA): - RFID tracking of patients/medical devices must protect PHI (Protected Health Information) - Encryption required for RFID data containing patient identifiers - Access controls and audit logging mandatory
Finance (PCI DSS): - RFID payment systems must comply with Payment Card Industry Data Security Standard - Cardholder data encryption in transit and at rest - Penetration testing of RFID payment terminals
Pharmaceuticals (DSCSA): - Drug Supply Chain Security Act requires serialized tracking - RFID commonly used for compliance - Data integrity and anti-counterfeiting measures required
Explore Related Learning Resources:
Knowledge Map Hub - Visualize relationships between RFID security concepts (authentication, encryption, privacy) and broader IoT security frameworks (zero trust, defense in depth, threat modeling)
Quizzes Hub - Test your understanding:
- RFID Security Quiz: Attack vectors, countermeasures, cost-benefit analysis
- Privacy Quiz: GDPR compliance, tracking scenarios, de-anonymization
- Protocol Quiz: Challenge-response, mutual auth, Gen 2v2 features
Simulations Hub - Interactive explorations:
- RFID Eavesdropping Range Simulator: Calculate interception distance vs. frequency/power
- Tag Selection Calculator: Compare cost/security trade-offs for deployment scenarios
- Privacy Risk Assessment Tool: Evaluate tracking/profiling risks in retail/workplace
Videos Hub - Visual learning:
- RFID Security Fundamentals: Attack demonstrations (cloning, relay attacks)
- Gen 2v2 Authentication: How challenge-response prevents unauthorized reads
- Privacy-Enhancing Technologies: Rolling codes, Faraday cages, blocker tags
Knowledge Gaps Hub - Common misconceptions:
- “Encryption makes RFID 100% secure” → Relay attacks bypass encryption
- “Kill command eliminates all privacy risks” → Default passwords enable abuse
- “Only passive tags are vulnerable” → Active tags susceptible to jamming/DoS
RFID-blocking sleeves can reduce the risk of opportunistic, close-range eavesdropping by attenuating the RF field, but they don’t address many real-world fraud paths.
What RFID blocking helps with: - Skimming-style reads when a card/passport is not being used (and the shield is properly covering it)
What it does not solve: - Relay attacks when the card is out of the shield (or the shield is incomplete/misused) - Compromised readers/terminals (you intentionally present the card to a device) - Card-not-present fraud and account compromise (online), which are unrelated to RFID
Practical guidance: - Prefer mobile wallets where available (tokenization + device authentication). - Enable transaction alerts and review statements regularly. - For passports and access badges, keep them in a shielded holder when not in use and choose systems with mutual authentication/anti-cloning protections.
Bottom line: Treat RFID blocking as a narrow, situational mitigation—not a complete security solution.
870.8 Knowledge Check
870.9 Visual Reference Gallery
Explore alternative visual representations of RFID security and attack vector concepts.
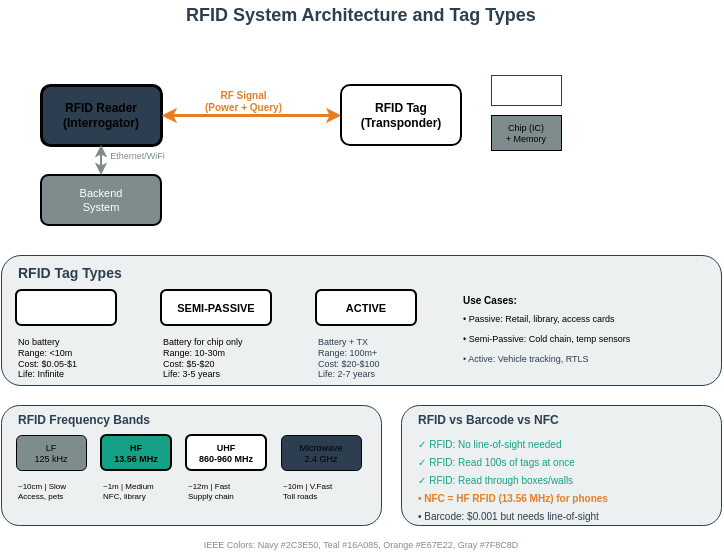
RFID systems consist of readers, tags, and backend infrastructure. Understanding this architecture is essential for identifying security vulnerabilities at each layer.
Different tag types offer varying security capabilities. Passive tags (no battery) have limited cryptographic capacity, while active tags can implement full AES encryption.
Active RFID provides longer range (100m+) and stronger security, while passive RFID offers lower cost for high-volume deployments with appropriate security controls.
870.10 Summary
- Attack surface: Eavesdropping, cloning/replay, relay (ghost/leech), DoS/jamming, and physical extraction—plus privacy risks from stable identifiers
- Defense-in-depth: Combine tag-level authentication/encryption with reader authorization, backend access control/logging, and physical range/shielding controls
- Privacy by design: Minimize stable IDs, limit read range, define retention/sharing policies, and map controls to regulatory requirements (GDPR/CCPA)
870.11 What’s Next
In the next chapter, RFID Comprehensive Review, we’ll synthesize RFID concepts with quiz questions, frequency band comparisons, and real-world deployment case studies.




