%% fig-alt: "Comprehensive defense in depth architecture showing eight hierarchical security layers in IoT systems, flowing from bottom physical layer to top monitoring layer. Layer 1 (Physical Security) provides tamper-evident enclosures and physical access control as foundation. Layer 2 (Network Perimeter) implements firewalls, intrusion detection/prevention systems (IDS/IPS), and VPN gateways. Layer 3 (Network Segmentation) isolates traffic using VLANs, DMZ zones, and zero-trust architecture principles. Layer 4 (Device Authentication) verifies device identity through certificates, two-factor authentication (2FA), and unique device credentials. Layer 5 (Authorization) enforces role-based access control (RBAC), least privilege principle, and granular permissions. Layer 6 (Data Encryption) protects information using TLS/DTLS protocols, AES encryption, and end-to-end encrypted channels. Layer 7 (Application Security) secures software through input validation, secure coding practices, and regular security patches. Layer 8 (Monitoring & Response) provides continuous oversight via Security Information and Event Management (SIEM), anomaly detection algorithms, and incident response procedures. Arrows show progressive security hardening from physical to logical layers, with final teal-highlighted monitoring layer providing continuous visibility across all seven underlying layers. Key principle: attacker breaching any single layer still faces six additional defensive barriers before reaching critical assets."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '13px'}}}%%
graph TB
subgraph "Defense in Depth Layers"
L1[Layer 1: Physical Security<br/>Tamper-evident enclosures, access control]
L2[Layer 2: Network Perimeter<br/>Firewall, IDS/IPS, VPN]
L3[Layer 3: Network Segmentation<br/>VLANs, DMZ, zero-trust architecture]
L4[Layer 4: Device Authentication<br/>Certificates, 2FA, device identity]
L5[Layer 5: Authorization<br/>RBAC, least privilege, access control]
L6[Layer 6: Data Encryption<br/>TLS/DTLS, AES, end-to-end encryption]
L7[Layer 7: Application Security<br/>Input validation, secure coding, patches]
L8[Layer 8: Monitoring & Response<br/>SIEM, anomaly detection, incident response]
end
L1 --> L2
L2 --> L3
L3 --> L4
L4 --> L5
L5 --> L6
L6 --> L7
L7 --> L8
style L1 fill:#2C3E50,stroke:#16A085,color:#fff
style L2 fill:#2C3E50,stroke:#16A085,color:#fff
style L3 fill:#2C3E50,stroke:#16A085,color:#fff
style L4 fill:#2C3E50,stroke:#16A085,color:#fff
style L5 fill:#2C3E50,stroke:#16A085,color:#fff
style L6 fill:#2C3E50,stroke:#16A085,color:#fff
style L7 fill:#2C3E50,stroke:#16A085,color:#fff
style L8 fill:#16A085,stroke:#0e6655,color:#fff
1382 Defense in Depth and Security Controls
1382.1 Learning Objectives
By the end of this chapter, you should be able to:
- Explain the defense-in-depth security model and its importance for IoT
- Identify and describe the eight layers of defense in IoT systems
- Categorize security controls as preventive, detective, or corrective
- Design layered security architectures that protect against multiple attack vectors
- Apply security controls at each layer of the IoT stack
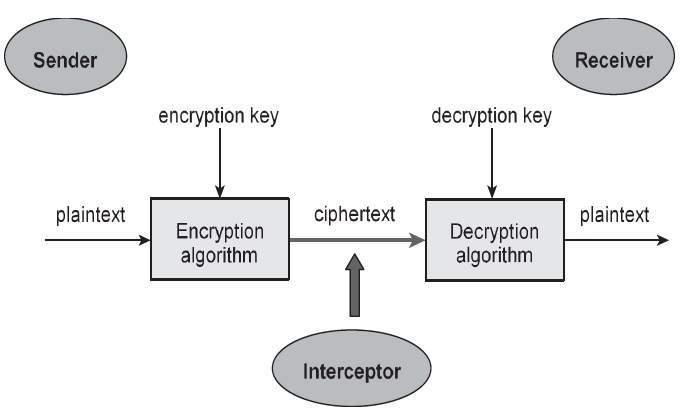
What is Defense in Depth? Defense in depth is a security strategy that uses multiple layers of protection, so if one layer fails, others still protect your system. Think of it like a medieval castle with walls, a moat, guards, and a keep - an attacker must bypass ALL defenses to succeed.
Why does it matter? No single security measure is perfect. Firewalls can be bypassed, passwords can be stolen, encryption keys can be compromised. By layering multiple independent security controls, you ensure that a single failure doesn’t result in complete compromise.
Key terms: | Term | Definition | |——|————| | Security Layer | An independent security control that provides protection at a specific level | | Preventive Control | Stops attacks before they happen (firewalls, encryption, access control) | | Detective Control | Identifies attacks in progress (IDS, logging, monitoring) | | Corrective Control | Fixes damage after an attack (backups, patches, incident response) |
1382.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Security and Privacy Overview: Foundational understanding of IoT security principles and the CIA triad
- Networking Basics: Understanding network protocols helps contextualize network-level security controls
1382.3 Defense in Depth Architecture
Security is not a single layer but multiple concentric defenses working together. The defense-in-depth model implements security controls at every layer of the IoT stack.
Key Principle: If an attacker breaches one layer (e.g., passes firewall), they still face six more layers of defense before reaching critical assets. Each layer detects, delays, or blocks attacks.
Core Concept: Defense in depth layers multiple independent security controls at different system levels so that failure of any single protection does not result in complete compromise. Why It Matters: IoT systems face attacks from multiple vectors simultaneously (network, physical, application); relying on a single strong control creates a single point of failure that determined attackers will eventually bypass. Key Takeaway: Always implement at least three overlapping security layers (e.g., network firewall + device authentication + data encryption) because attackers who bypass one control still face additional barriers before reaching critical assets.
1382.3.1 The Eight Security Layers Explained
| Layer | Purpose | Example Controls | Attack It Prevents |
|---|---|---|---|
| Physical Security | Prevent unauthorized physical access | Tamper-evident cases, locked enclosures, security cameras | Device theft, hardware tampering |
| Network Perimeter | Filter traffic at network boundary | Firewalls, IDS/IPS, VPN gateways | Network intrusion, unauthorized access |
| Network Segmentation | Isolate different network zones | VLANs, DMZ, microsegmentation | Lateral movement after breach |
| Device Authentication | Verify device identity | X.509 certificates, device tokens, mTLS | Device impersonation, rogue devices |
| Authorization | Control what authenticated entities can do | RBAC, ABAC, ACLs | Privilege escalation, unauthorized actions |
| Data Encryption | Protect data confidentiality | TLS/DTLS, AES, end-to-end encryption | Eavesdropping, data theft |
| Application Security | Secure application code | Input validation, secure coding, patches | SQL injection, buffer overflow |
| Monitoring & Response | Detect and respond to incidents | SIEM, anomaly detection, incident response | Undetected breaches, slow response |
1382.3.2 Real-World Example: Why One Layer Isn’t Enough
Imagine your smart home with ONLY one security method:
| Only Using | What Happens When It Fails |
|---|---|
| Only encryption | Encryption key is hardcoded → attacker extracts it → game over |
| Only authentication | Password is phished → attacker logs in → full access |
| Only authorization | Account is hijacked → limited damage, but still compromised |
| Only monitoring | Attack detected, but no prevention → damage already done |
Defense in Depth: Multiple layers working together
%% fig-alt: "Defense in depth flowchart showing layered security model with six consecutive defensive barriers that an attacker must penetrate. Attack flow begins with attacker encountering Layer 1 (Firewall blocking unauthorized IPs). If bypassed, attacker faces Layer 2 (Authentication verifying credentials). If compromised, Layer 3 (Authorization checking permissions) validates access rights. If escalated, Layer 4 (Encryption protecting data) secures information. If encryption key is extracted, Layer 5 (Monitoring detecting anomalies) identifies suspicious activity. If monitoring is evaded, final Layer 6 (Incident Response containing damage) limits impact. Each successive layer provides backup protection if previous layer fails, demonstrating that security depends on multiple overlapping controls rather than single point of defense. Attacker shown in red must overcome all six green/navy security layers, with final incident response layer highlighted in teal as last line of defense."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '14px'}}}%%
graph TD
A[Attacker] -->|Layer 1| B[Firewall<br/>Block unauthorized IPs]
B -->|Bypassed| C[Authentication<br/>Verify credentials]
C -->|Compromised| D[Authorization<br/>Check permissions]
D -->|Escalated| E[Encryption<br/>Protect data]
E -->|Key extracted| F[Monitoring<br/>Detect anomalies]
F -->|Evaded| G[Incident Response<br/>Contain damage]
style A fill:#e74c3c,stroke:#c0392b,color:#fff
style B fill:#2C3E50,stroke:#16A085,color:#fff
style C fill:#2C3E50,stroke:#16A085,color:#fff
style D fill:#2C3E50,stroke:#16A085,color:#fff
style E fill:#2C3E50,stroke:#16A085,color:#fff
style F fill:#2C3E50,stroke:#16A085,color:#fff
style G fill:#16A085,stroke:#0e6655,color:#fff
Each layer provides a second chance if the previous layer fails.
Question: A smart factory’s firewall is compromised by an attacker. Which defense-in-depth principle explains why this single breach should NOT give the attacker full control of all industrial systems?
Click to reveal answer
Answer: Multiple independent security layers ensure attackers must bypass additional controls (authentication, encryption, monitoring) after passing the firewall.
Why? Defense in depth means each layer (network, device authentication, data encryption, access control, monitoring) operates independently. Even if the firewall fails, attackers still face device certificates, encrypted communications, role-based access control, and intrusion detection systems.
1382.4 Security Controls Framework
Security controls are categorized by their function in the security lifecycle: preventing attacks before they occur, detecting attacks in progress, and correcting damage after attacks.
%% fig-alt: "Security controls framework showing three complementary control types forming complete security lifecycle with feedback loop. Preventive Controls (navy) stop attacks before they occur through proactive measures including firewalls blocking malicious traffic, encryption protecting data confidentiality, and access control restricting unauthorized entry. If preventive controls are bypassed, Detective Controls (orange) identify attacks in progress using intrusion detection systems (IDS), comprehensive logging of security events, continuous monitoring of system behavior, and Security Information and Event Management (SIEM) correlation. When detective controls trigger alerts, Corrective Controls (teal) remediate damage after attacks through data restoration from backups, security patch deployment to close vulnerabilities, and structured incident response procedures to contain and recover from breaches. Final feedback arrow from corrective to preventive represents lessons learned cycle where post-incident analysis strengthens future preventive measures. Diagram demonstrates defense in depth philosophy: each control type has distinct function (prevent, detect, or correct) but all work together continuously."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'fontSize': '14px'}}}%%
graph LR
subgraph "Security Control Types"
P[Preventive Controls<br/>Stop attacks before they happen<br/>Firewalls, encryption, access control]
D[Detective Controls<br/>Identify attacks in progress<br/>IDS, logging, monitoring, SIEM]
C[Corrective Controls<br/>Fix damage after attack<br/>Backups, patches, incident response]
end
P -->|If bypassed| D
D -->|Alert triggered| C
C -->|Lessons learned| P
style P fill:#2C3E50,stroke:#16A085,color:#fff
style D fill:#E67E22,stroke:#d35400,color:#fff
style C fill:#16A085,stroke:#0e6655,color:#fff
1382.4.1 Preventive Controls
Purpose: Stop attacks before they occur
| Control Type | Description | IoT Example |
|---|---|---|
| Firewalls | Filter network traffic based on rules | Block all inbound traffic except port 8883 (MQTT) |
| Encryption | Protect data confidentiality | AES-256 encryption of sensor data |
| Access Control | Restrict who can do what | Only admins can change device configuration |
| Input Validation | Reject malicious input | Reject MQTT messages with invalid JSON |
| Secure Boot | Ensure only trusted code runs | Verify firmware signature before execution |
1382.4.2 Detective Controls
Purpose: Identify attacks in progress
| Control Type | Description | IoT Example |
|---|---|---|
| Intrusion Detection (IDS) | Monitor for attack signatures | Alert on port scanning attempts |
| Logging | Record security events | Log all authentication attempts |
| Anomaly Detection | Identify unusual behavior | Flag sensor sending 100x normal data volume |
| SIEM | Correlate events across systems | Detect coordinated attack across multiple devices |
| File Integrity Monitoring | Detect unauthorized changes | Alert if firmware hash changes |
1382.4.3 Corrective Controls
Purpose: Fix damage after an attack
| Control Type | Description | IoT Example |
|---|---|---|
| Backups | Restore data after loss | Restore device configuration from backup |
| Patches | Fix vulnerabilities | Deploy security update to all devices |
| Incident Response | Structured recovery process | Isolate compromised device, analyze, remediate |
| Rollback | Revert to known-good state | Restore previous firmware version |
| Quarantine | Isolate compromised systems | Move infected device to isolated VLAN |
1382.4.4 Security Controls by IoT Layer
This view maps security control types to specific IoT architecture layers:
%% fig-alt: "Security controls matrix showing preventive detective and corrective controls at each IoT layer: Device layer uses secure boot, firmware verification, anomaly detection, and recovery partitions; Network layer uses firewalls, TLS encryption, IDS/IPS, and network isolation; Application layer uses input validation, API authentication, logging, and patch management; Data layer uses encryption at rest, access control, audit trails, and backup restoration. Each layer requires all three control types for complete protection."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart TB
subgraph Controls["SECURITY CONTROLS BY LAYER"]
subgraph Device["DEVICE LAYER"]
DP["Preventive:<br/>Secure Boot<br/>Firmware Signing"]
DD["Detective:<br/>Anomaly Detection<br/>Health Monitoring"]
DC["Corrective:<br/>Recovery Partition<br/>Auto-rollback"]
end
subgraph Network["NETWORK LAYER"]
NP["Preventive:<br/>Firewall<br/>TLS/DTLS"]
ND["Detective:<br/>IDS/IPS<br/>Traffic Analysis"]
NC["Corrective:<br/>Network Isolation<br/>Traffic Blocking"]
end
subgraph App["APPLICATION LAYER"]
AP["Preventive:<br/>Input Validation<br/>API Auth"]
AD["Detective:<br/>WAF Logging<br/>Error Monitoring"]
AC["Corrective:<br/>Patch Deployment<br/>Service Restart"]
end
subgraph Data["DATA LAYER"]
DaP["Preventive:<br/>Encryption<br/>Access Control"]
DaD["Detective:<br/>Audit Trails<br/>Integrity Checks"]
DaC["Corrective:<br/>Backup Restore<br/>Data Recovery"]
end
end
Device --> Network --> App --> Data
style DP fill:#2C3E50,stroke:#16A085,color:#fff
style DD fill:#E67E22,stroke:#d35400,color:#fff
style DC fill:#16A085,stroke:#0e6655,color:#fff
style NP fill:#2C3E50,stroke:#16A085,color:#fff
style ND fill:#E67E22,stroke:#d35400,color:#fff
style NC fill:#16A085,stroke:#0e6655,color:#fff
style AP fill:#2C3E50,stroke:#16A085,color:#fff
style AD fill:#E67E22,stroke:#d35400,color:#fff
style AC fill:#16A085,stroke:#0e6655,color:#fff
style DaP fill:#2C3E50,stroke:#16A085,color:#fff
style DaD fill:#E67E22,stroke:#d35400,color:#fff
style DaC fill:#16A085,stroke:#0e6655,color:#fff
Complete IoT security requires all three control types (preventive, detective, corrective) at every architectural layer.
1382.4.5 Example Scenario: SQL Injection Attack
An attacker attempts SQL injection on an IoT dashboard:
- Preventive Control: Input validation rejects malicious SQL characters → Attack stopped
- Detective Control: If bypassed, Web Application Firewall (WAF) logs unusual query patterns → Alert triggered
- Corrective Control: Security team patches vulnerability, reviews logs, and restores any corrupted data
1382.5 Real-World Security Failures
1382.5.1 The Industrial Plant Attack (2014)
Location: German steel mill
What happened:
- Attackers used phishing to steal employee credentials (failed authentication)
- Once inside the network, attackers had full access to industrial controls (failed authorization)
- Attackers disabled safety systems and caused a blast furnace to malfunction
- Result: Massive physical damage to the plant
Which security methods failed?
| Method | What Failed | What Should Have Been Done |
|---|---|---|
| Authentication | Simple password, no 2FA | Multi-factor authentication (password + hardware token) |
| Authorization | Employee account had admin access to everything | Least privilege (employees only access what they need) |
| Monitoring | No detection of abnormal commands | Intrusion detection system (alert on unusual commands) |
| Segmentation | Office network connected to industrial control network | Air gap or firewall between office and industrial networks |
Lesson: Authentication alone is not enough. You need authorization, monitoring, and network segmentation too.
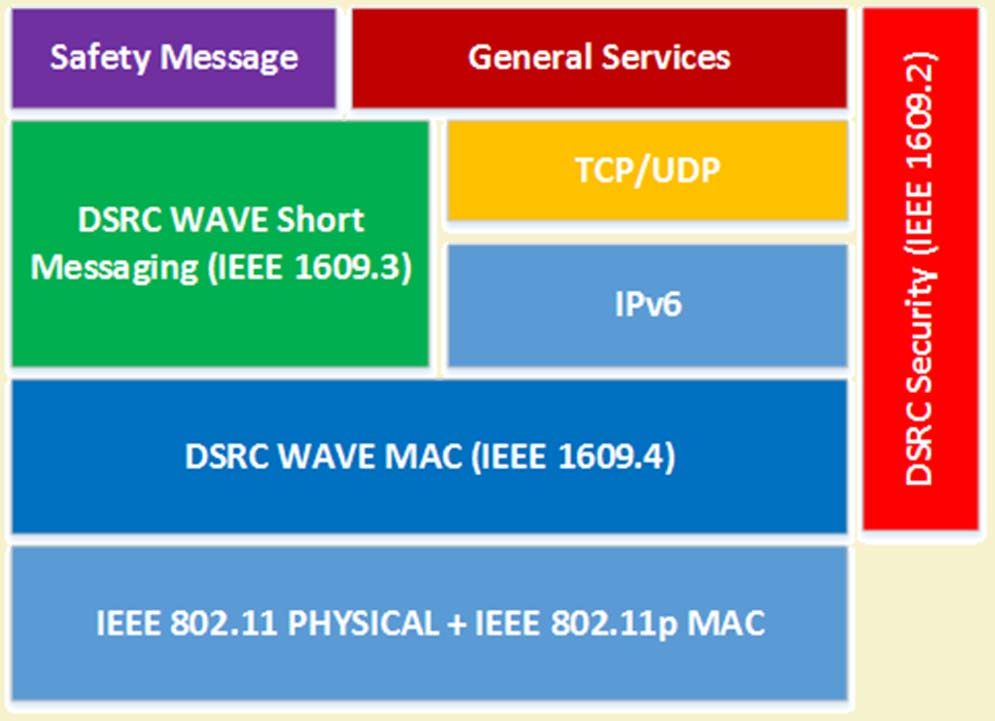
Source: NPTEL Internet of Things Course, IIT Kharagpur - This DSRC WAVE protocol stack illustrates a key security principle: security (IEEE 1609.2) is integrated as a vertical layer spanning all protocol layers, demonstrating defense-in-depth architecture where security is not bolted on but built into every communication layer.
1382.6 Chapter Summary
Defense in depth is the foundational security strategy for IoT systems, implementing multiple independent security controls at every layer of the architecture. The eight-layer model (physical, network perimeter, segmentation, authentication, authorization, encryption, application, monitoring) ensures that failure of any single control doesn’t result in complete system compromise.
Security controls fall into three categories: preventive controls that stop attacks before they occur, detective controls that identify attacks in progress, and corrective controls that remediate damage after attacks. Effective IoT security requires all three control types working together at every architectural layer.
Real-world incidents like the German steel mill attack demonstrate the consequences of relying on single security measures. Organizations that implement layered defenses with multiple overlapping controls significantly reduce their attack surface and improve their ability to detect, contain, and recover from security incidents.
1382.7 What’s Next
With the defense-in-depth framework established, the next chapter examines Cryptography for IoT where you’ll learn the specific cryptographic techniques (AES, RSA, ECC, hashing) that implement encryption at various security layers.
Continue to Cryptography for IoT →
