1365 IoT Security Practice and Assessment
1365.1 Introduction
This section provides comprehensive practical resources for IoT security including hands-on labs, exam preparation materials, and advanced technical concepts. The content has been organized into focused chapters for effective learning.
1365.2 Visual Reference Gallery
These AI-generated figures provide alternative visual perspectives on security and privacy concepts, rendered using the IEEE color palette (Navy #2C3E50, Teal #16A085, Orange #E67E22).
The IoT security landscape spans multiple layers, each presenting unique attack surfaces that require coordinated defense strategies to protect connected systems comprehensively.
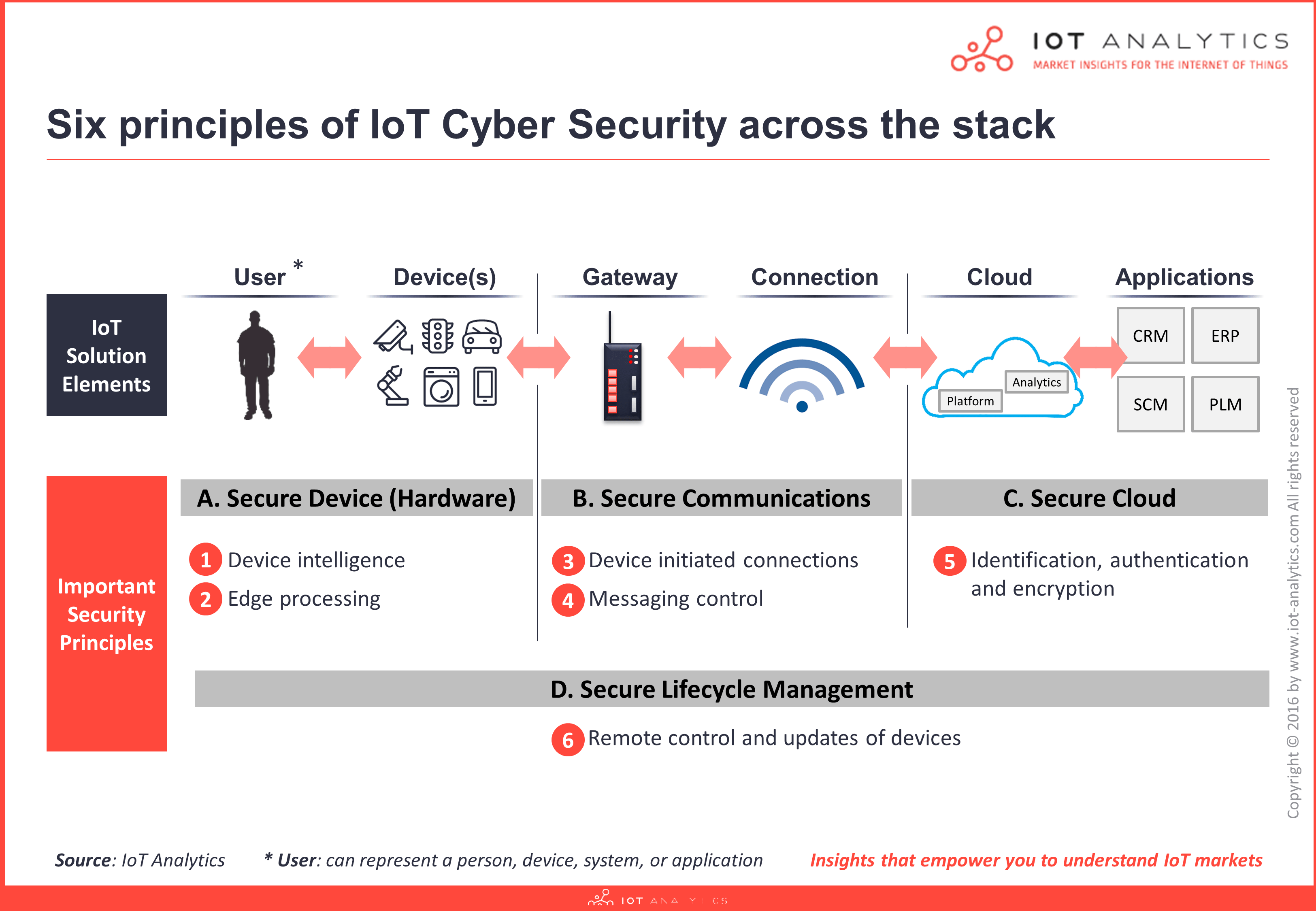
The seven-layer IoT reference model provides a framework for understanding where security controls must be implemented, from physical device hardening through secure edge processing to protected cloud services.
STRIDE provides a comprehensive framework for systematic threat identification, ensuring security assessments consider all major attack categories relevant to IoT systems.
Zero trust architecture eliminates implicit trust in IoT networks, requiring continuous verification of every device and request regardless of network location or previous authentication state.
1365.3 Chapter Structure
This practice section is organized into three focused chapters:
1365.3.1 1. Security Practice Labs
Time: ~60 min | Level: Intermediate-Advanced
Hands-on security assessment labs:
- Lab 1: IoT device security audit checklist (physical, network, authentication, firmware, privacy)
- Lab 2: Network segmentation for IoT devices (guest network and VLAN configuration)
- Lab 3: HTTPS certificate verification using OpenSSL and browser tools
Key Takeaway: Practical skills developed through hands-on labs translate directly to real-world security assessments.
1365.3.2 2. Exam Preparation Guide
Time: ~45 min | Level: Advanced
Comprehensive study materials:
- Key concepts to master (CIA triad, OWASP Top 10, defense-in-depth)
- Memory aids and mnemonics for exam recall
- Practice problems with detailed solutions
- Time management strategies for different question types
- Common mistakes and red flags to avoid
Key Takeaway: Structured exam preparation with practice problems builds confidence and ensures concept mastery.
1365.3.3 3. Advanced Security Concepts
Time: ~50 min | Level: Advanced
Deep technical knowledge:
- Cryptographic strength and brute-force analysis
- Secure boot chain of trust implementation
- TLS 1.3 vs DTLS performance comparison
- STRIDE threat modeling methodology
- Side-channel attacks and mitigations
Key Takeaway: Understanding security at a technical level enables design of production-grade secure systems.
1365.4 Alternative Source Figures
Source: CP IoT System Design Guide, Chapter 6 - Security and Privacy
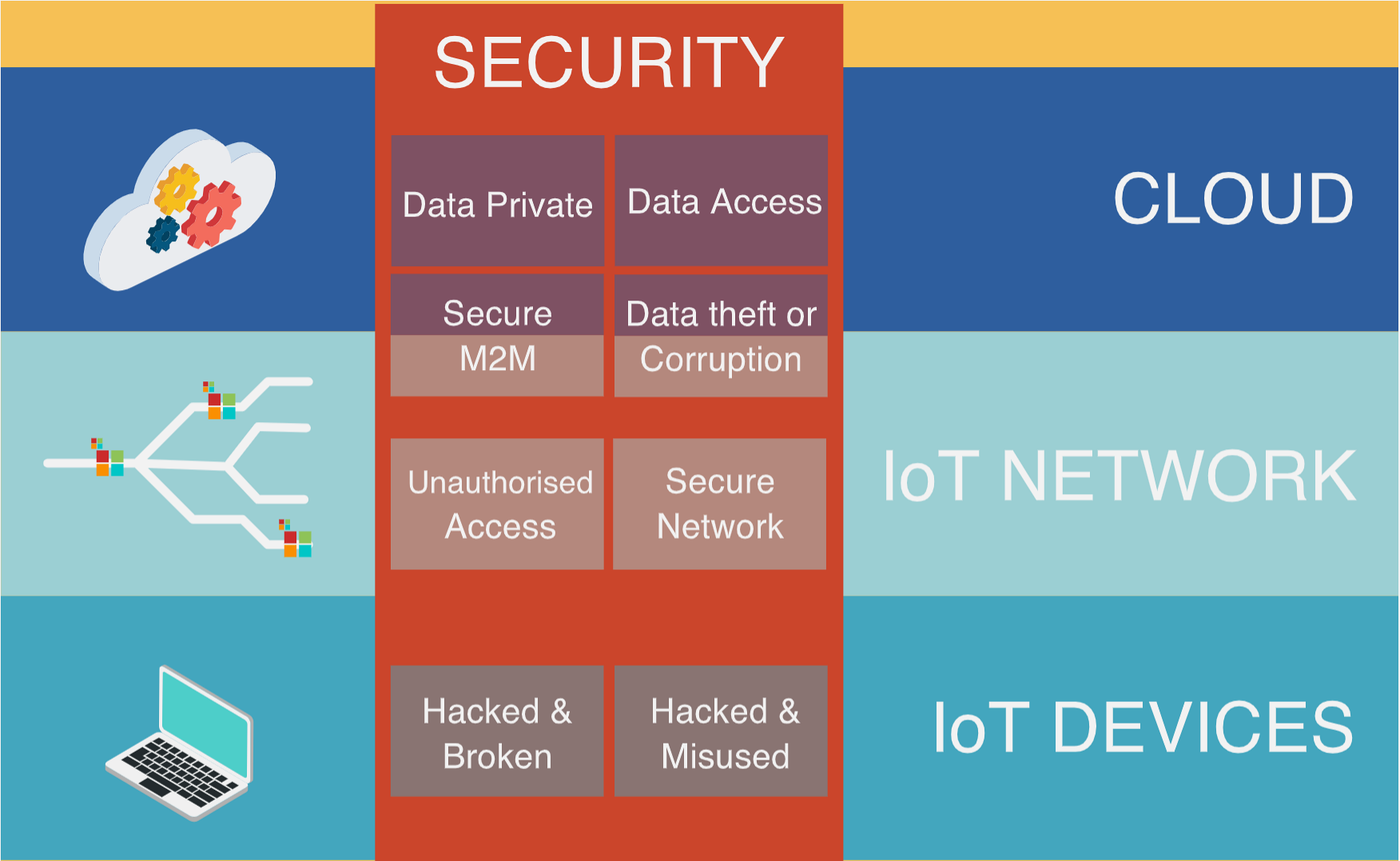
Source: CP IoT System Design Guide, Chapter 5 - Data Security
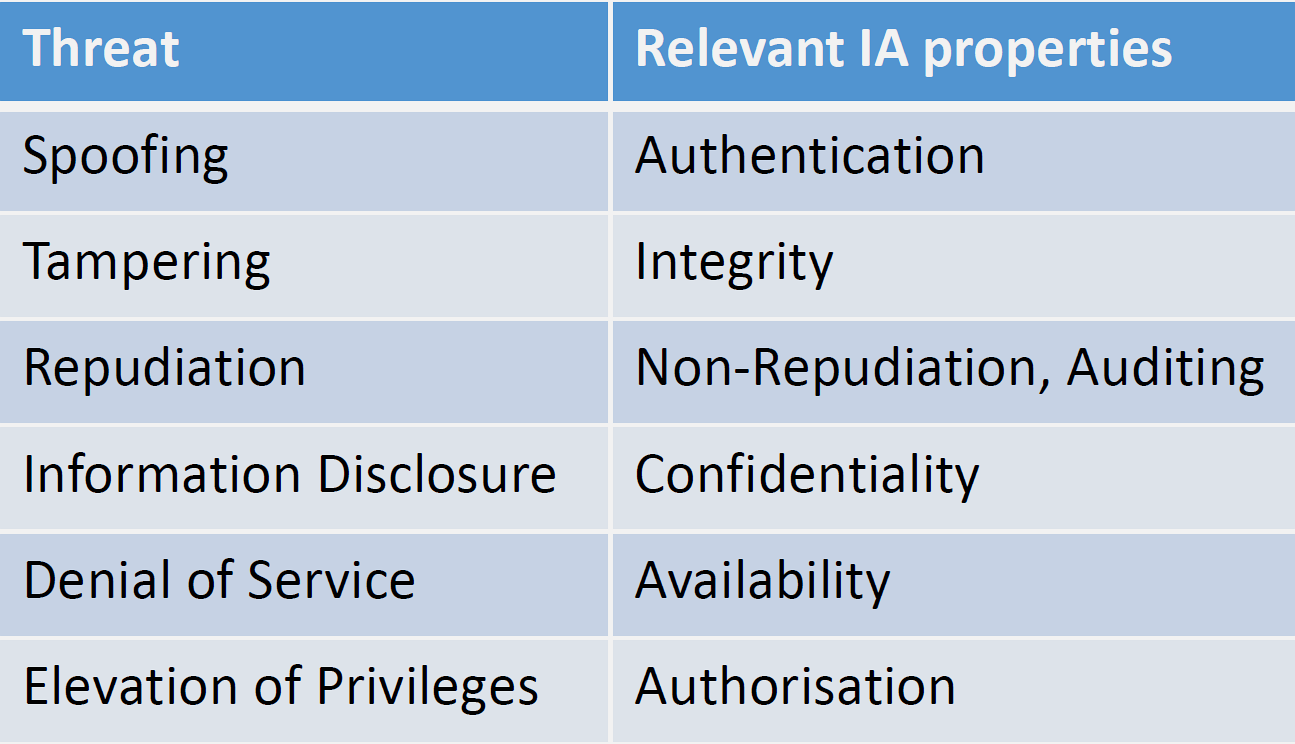
Source: CP IoT System Design Guide, Chapter 6 - Security and Privacy
1365.5 What’s Next
Based on what you learned about IoT security fundamentals and the CIA triad:
- For hands-on practice: Security Practice Labs - Apply skills with real tools and checklists
- For exam preparation: Exam Preparation Guide - Study strategies and practice problems
- For advanced theory: Advanced Security Concepts - Cryptography, secure boot, STRIDE modeling
- To go deeper: Cyber Security Methods - Encryption, authentication, and secure communication protocols
- To apply it: Zero-Trust Security - Design networks that verify every request
1365.6 Summary
This practice section provides the hands-on component of IoT security learning:
- Labs: Develop practical skills through device audits, network segmentation, and certificate verification
- Exam Prep: Build confidence with structured study materials and practice problems
- Advanced Concepts: Understand security at a technical level for production system design
Complete these chapters to transform security knowledge into practical competence.
