Attack Scenario Details
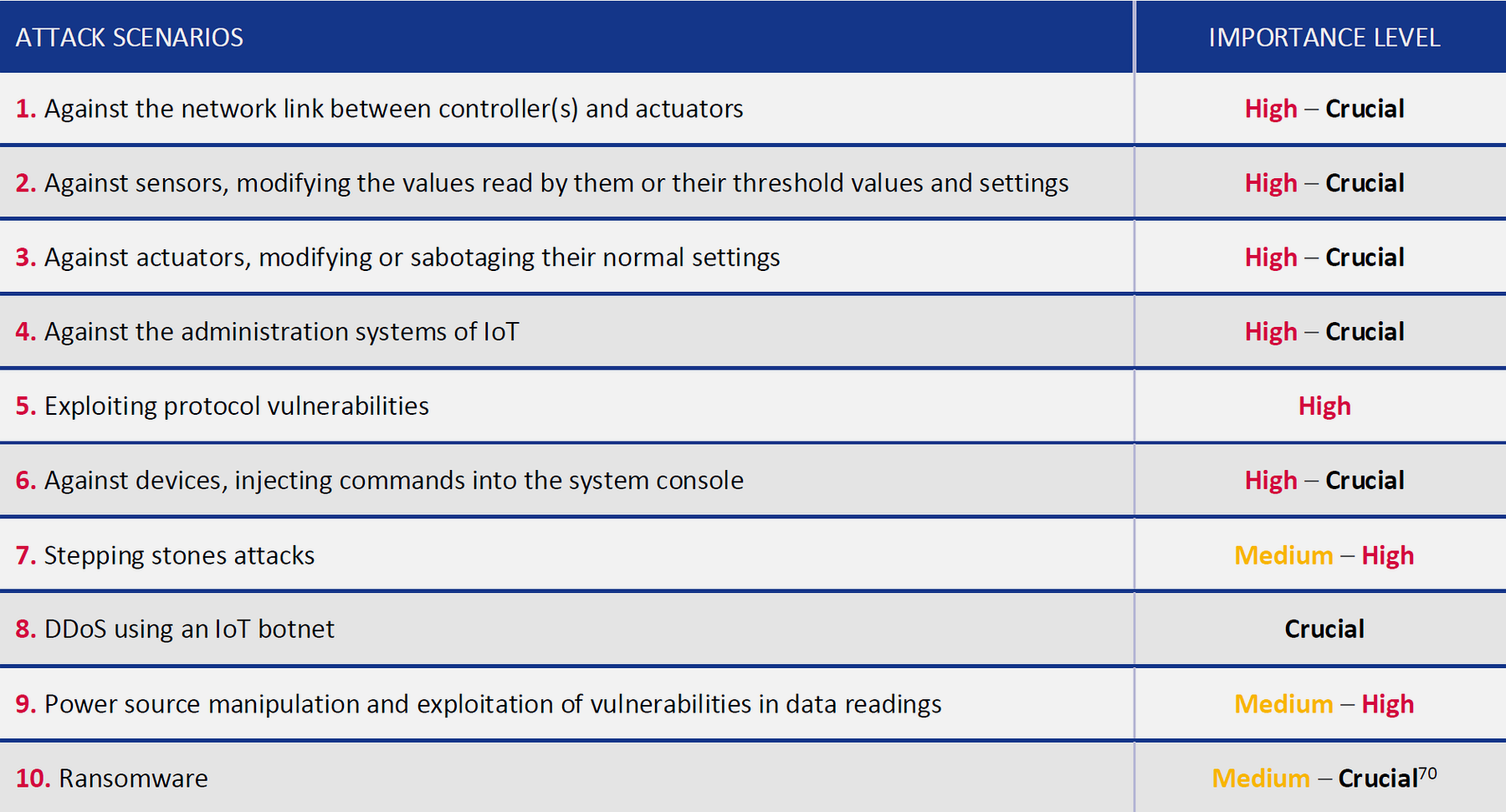
1. Network Link Eavesdropping
Target: Communication between controllers and actuators
Attack: Passive interception of network traffic to extract sensitive operational information
Impact: - Data leakage - Intelligence gathering for Advanced Persistent Threats (APTs) - Identification of weak spots for future attacks
Mitigation: - End-to-end encryption (TLS/DTLS) - Network segmentation - Intrusion detection systems - Regular traffic analysis
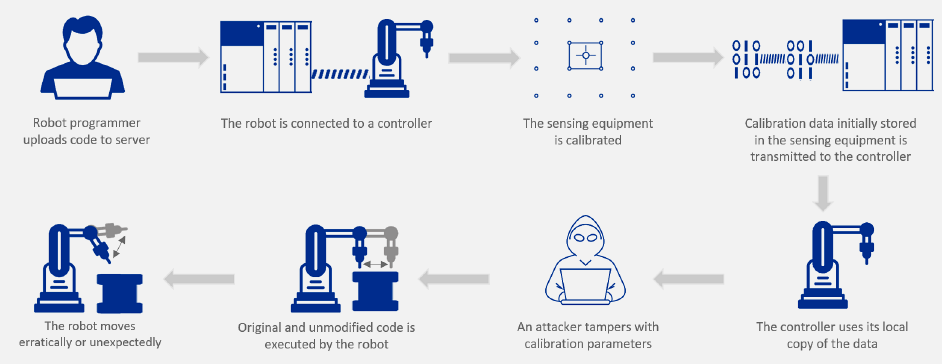
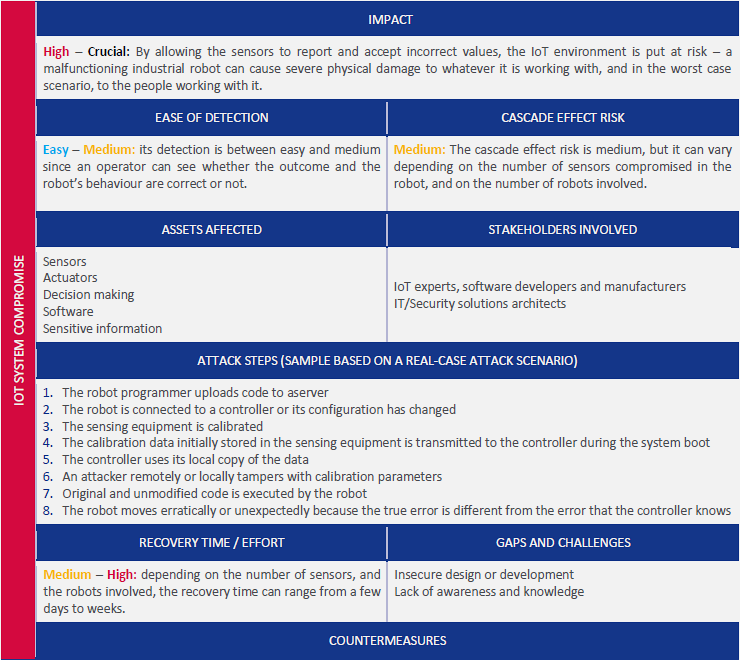
2. Sensor Manipulation
Target: Sensor threshold values and configuration
Attack: Modify calibration parameters to accept out-of-range values
Impact: - Incorrect sensor readings - Safety system failures - Physical damage to equipment (e.g., power spikes)
Mitigation: - Tamper-resistant hardware - Integrity checking of configuration - Multiple redundant sensors - Anomaly detection algorithms
3. Actuator Sabotage
Target: Actuator configuration and operational parameters
Attack: Modify settings to cause malfunction or incorrect operation
Impact: - Production disruptions - Safety hazards - Equipment damage - Environmental incidents
Mitigation: - Command authentication - Configuration validation - Physical access controls - Fail-safe mechanisms
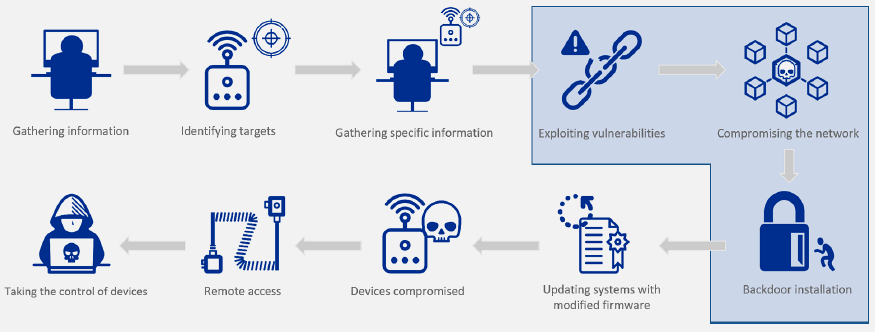
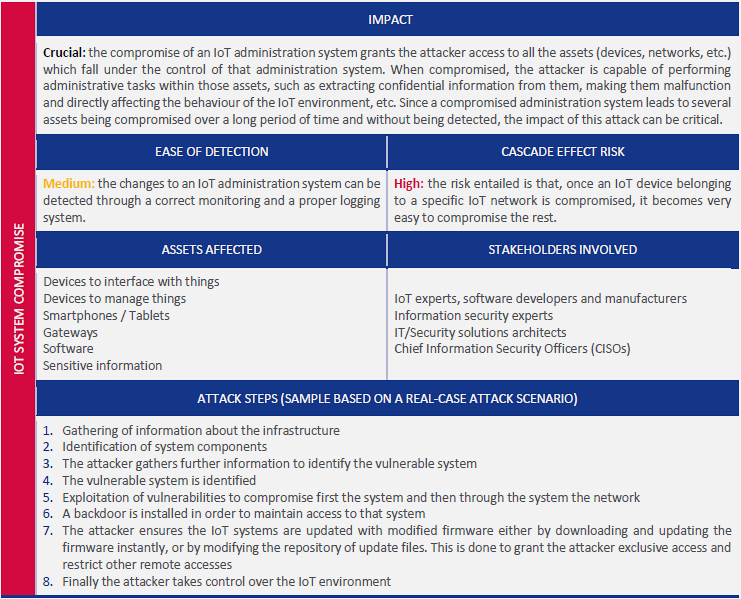
4. Administration System Compromise
Target: IoT device management systems
Attack: Gain full control via weak/default credentials, then modify entire deployment
Impact: - Complete system compromise - Mass device manipulation - Network-wide disruption - Cascading failures
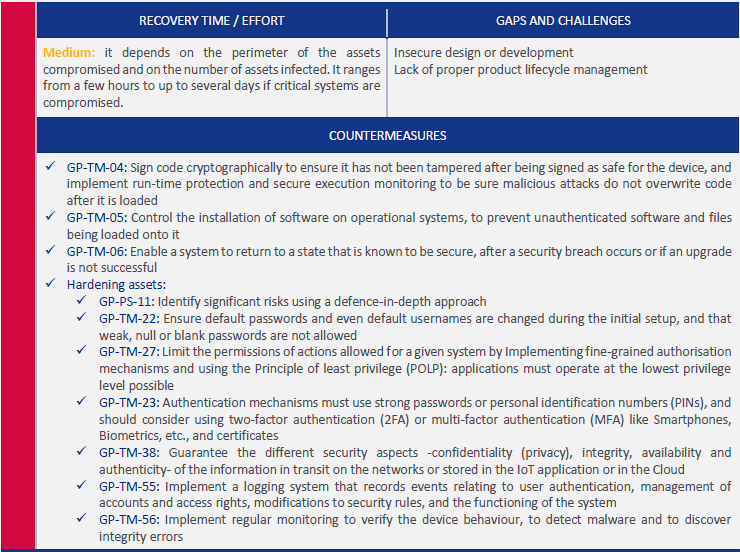
Mitigation: - Strong authentication (MFA) - Regular credential rotation - Principle of least privilege - Network segmentation
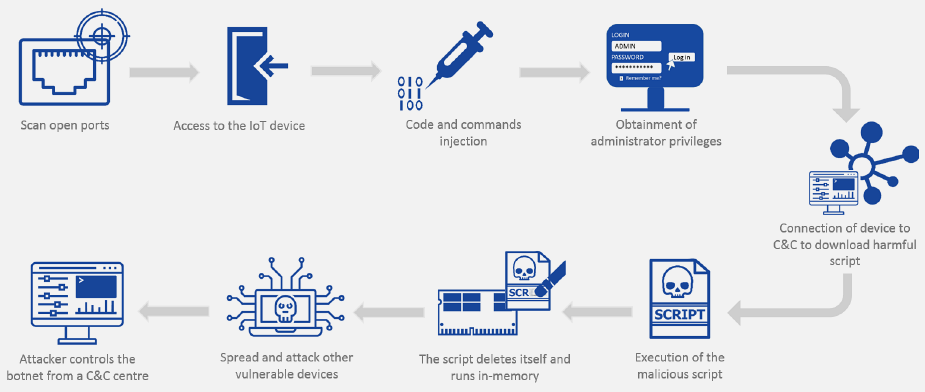
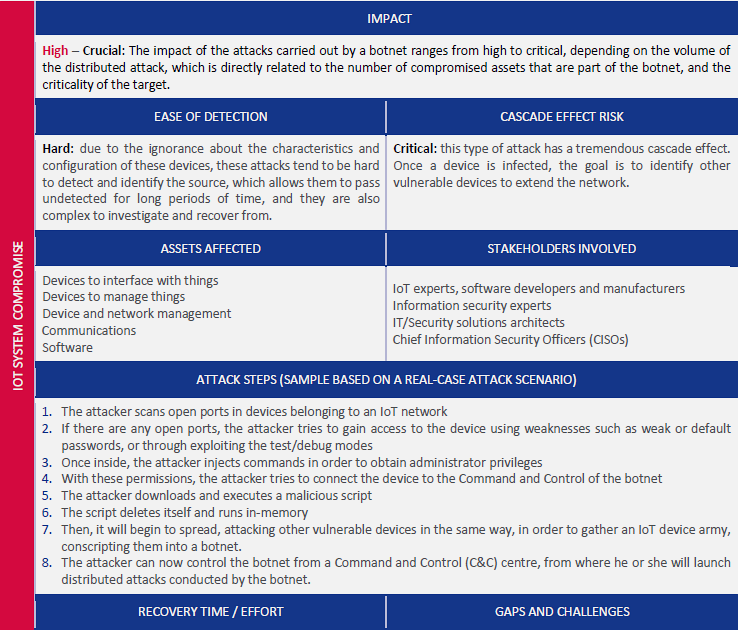
8. DDoS Using IoT Botnet
Target: External services using compromised IoT devices
Attack: Mirai-style botnet creation for distributed attacks
Impact: - Service unavailability for victims - Network bandwidth exhaustion - Reputation damage - Legal liability
Mitigation: - Secure default configurations - Automatic security updates - Network traffic monitoring - Bot detection systems
10. Ransomware
Target: IoT devices and data
Attack: Malware blocks access to data/functionality until ransom paid
Impact: - Critical service disruption - Safety risks (medical devices, thermostats, power grids) - Financial losses - Public safety threats
Mitigation: - Regular backups - Offline recovery systems - Security patching - User awareness training