%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'clusterBkg': '#f9f9f9', 'clusterBorder': '#2C3E50', 'edgeLabelBackground':'#ffffff'}}}%%
flowchart TB
A[IDENTIFY<br/>List Valuables] --> B[PROTECT<br/>Lock Doors & Windows]
B --> C[DETECT<br/>Motion Sensors & Alarms]
C --> D[RESPOND<br/>Call Police]
D --> E[RECOVER<br/>Insurance Claim]
A1[IoT: Inventory devices<br/>& identify sensitive data] -.-> A
B1[IoT: Encryption,<br/>firewalls, passwords] -.-> B
C1[IoT: Intrusion detection,<br/>anomaly monitoring] -.-> C
D1[IoT: Isolate compromised<br/>device, alert admin] -.-> D
E1[IoT: Restore from backup,<br/>patch vulnerability] -.-> E
style A fill:#2C3E50,stroke:#16A085,color:#fff
style B fill:#16A085,stroke:#2C3E50,color:#fff
style C fill:#E67E22,stroke:#2C3E50,color:#fff
style D fill:#E67E22,stroke:#2C3E50,color:#fff
style E fill:#16A085,stroke:#2C3E50,color:#fff
1448 NIST Cybersecurity Framework for IoT
1448.1 Learning Objectives
By the end of this chapter, you will be able to:
- Apply NIST Framework: Implement the five core functions (Identify, Protect, Detect, Respond, Recover) for IoT security
- Understand McCumber Cube: Apply the 3D security model combining CIA triad, data states, and countermeasures
- Assess Maturity Levels: Evaluate organizational security posture using NIST maturity tiers
- Balance Prevention vs Detection: Make informed decisions about security resource allocation
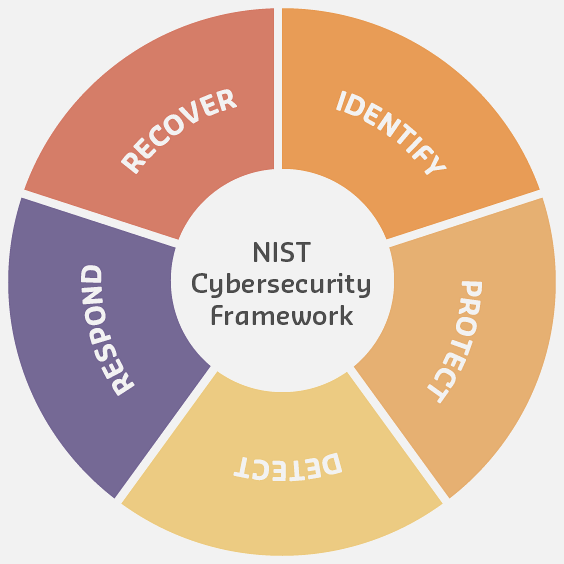
What is the NIST Cybersecurity Framework? The NIST Framework is a structured approach to managing cybersecurity risks, developed by the U.S. National Institute of Standards and Technology. It organizes security activities into five functions: Identify (know your assets and risks), Protect (implement defenses), Detect (monitor for threats), Respond (act on incidents), and Recover (restore services).
Why does it matter? No single security control is perfect - layered safeguards ensure that compromising one layer doesn’t breach the entire system. The framework provides a comprehensive approach that works for organizations of any size.
Key terms: | Term | Definition | |——|————| | NIST Framework | Five-function cybersecurity framework: Identify, Protect, Detect, Respond, Recover | | CIA Triad | Core security goals: Confidentiality, Integrity, Availability | | McCumber Cube | 3D security model combining CIA triad, data states, and countermeasures | | Defense in Depth | Layering multiple independent controls for comprehensive protection |
In one sentence: Effective IoT security requires the NIST Framework’s five functions - Identify, Protect, Detect, Respond, Recover - working together as layered defenses.
Remember this rule: No single security control is sufficient; layer technology, policy, and people safeguards across all data states because attackers will find and exploit the weakest link.
1448.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Security and Privacy Overview: Understanding of the CIA triad and IoT-specific security challenges
- Encryption Principles: Knowledge of encryption algorithms and cryptographic protocols
- Threat Modelling: Familiarity with identifying threats and attack vectors
1448.3 The Home Security Analogy
The NIST Cybersecurity Framework uses 5 functions. Here’s how they relate to home security:
1448.3.1 Applying This to IoT
| NIST Function | Home Example | IoT Example |
|---|---|---|
| Identify | List your valuables | Inventory all IoT devices, identify sensitive data |
| Protect | Lock doors | Use encryption, strong passwords, firewalls |
| Detect | Motion sensors | Network monitoring, anomaly detection, logs |
| Respond | Call police | Isolate compromised device, alert admin |
| Recover | Insurance claim | Restore from backup, patch vulnerability |
1448.4 NIST Cybersecurity Framework
The U.S. National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a comprehensive approach to managing cybersecurity risks, applicable to IoT devices and systems.
1448.4.1 Five Core Functions
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'clusterBkg': '#f9f9f9', 'clusterBorder': '#2C3E50', 'edgeLabelBackground':'#ffffff'}}}%%
flowchart LR
subgraph NIST["NIST Cybersecurity Framework"]
direction TB
A[IDENTIFY<br/>Asset Management<br/>Risk Assessment]
B[PROTECT<br/>Access Control<br/>Data Security<br/>Training]
C[DETECT<br/>Monitoring<br/>Anomaly Detection<br/>IDS/IPS]
D[RESPOND<br/>Response Planning<br/>Incident Analysis<br/>Mitigation]
E[RECOVER<br/>Recovery Planning<br/>Service Restoration<br/>Improvements]
end
A --> B
B --> C
C --> D
D --> E
E -.-> |Continuous Improvement| A
style A fill:#2C3E50,stroke:#16A085,color:#fff
style B fill:#16A085,stroke:#2C3E50,color:#fff
style C fill:#E67E22,stroke:#2C3E50,color:#fff
style D fill:#E67E22,stroke:#2C3E50,color:#fff
style E fill:#16A085,stroke:#2C3E50,color:#fff
1. IDENTIFY
- Purpose: Understand organizational context, resources, and risks
- Activities:
- Asset management (inventory of devices, data, systems)
- Business environment assessment
- Governance policies
- Risk assessment and management strategy
- Supply chain risk management
2. PROTECT
- Purpose: Implement safeguards to ensure service delivery
- Activities:
- Identity management and access control
- Data security (encryption, backups)
- Information protection processes
- Protective technology deployment
- Security awareness training
3. DETECT
- Purpose: Identify cybersecurity events promptly
- Activities:
- Anomalies and events monitoring
- Continuous security monitoring
- Detection processes
- Intrusion detection systems (IDS)
- Log analysis and correlation
4. RESPOND
- Purpose: Take action on detected cybersecurity incidents
- Activities:
- Response planning
- Communications (internal, external, stakeholders)
- Analysis of incidents
- Mitigation actions
- Improvements based on lessons learned
5. RECOVER
- Purpose: Restore capabilities impaired by incidents
- Activities:
- Recovery planning
- Improvements integration
- Communications during recovery
- Service restoration prioritization
- Post-incident analysis
1448.4.2 NIST Maturity Assessment
This view helps assess your organization’s maturity level for each NIST function, guiding improvement priorities:
%% fig-alt: "NIST Framework maturity assessment showing four tiers: Partial, Risk Informed, Repeatable, and Adaptive."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart TB
subgraph MATURITY["NIST MATURITY LEVELS"]
T1["TIER 1: PARTIAL<br/>Ad-hoc, reactive<br/>No formal processes"]
T2["TIER 2: RISK INFORMED<br/>Documented processes<br/>Management approved"]
T3["TIER 3: REPEATABLE<br/>Standardized processes<br/>Organization-wide"]
T4["TIER 4: ADAPTIVE<br/>Continuous improvement<br/>Lessons integrated"]
end
subgraph ASSESS["FUNCTION ASSESSMENT"]
ID["IDENTIFY<br/>Asset inventory?<br/>Risk assessment?"]
PR["PROTECT<br/>Access controls?<br/>Training program?"]
DE["DETECT<br/>Monitoring coverage?<br/>Alert response time?"]
RS["RESPOND<br/>Incident playbooks?<br/>Communication plan?"]
RC["RECOVER<br/>Backup tested?<br/>Recovery time?"]
end
T1 --> T2 --> T3 --> T4
ID --> GAP["GAP ANALYSIS<br/>Identify weakest<br/>functions first"]
PR --> GAP
DE --> GAP
RS --> GAP
RC --> GAP
GAP --> PRIORITY["IMPROVEMENT PRIORITY<br/>Lowest tier functions<br/>get resources first"]
style T1 fill:#e74c3c,stroke:#c0392b,color:#fff
style T2 fill:#E67E22,stroke:#d35400,color:#fff
style T3 fill:#f39c12,stroke:#d68910,color:#000
style T4 fill:#16A085,stroke:#0e6655,color:#fff
style ID fill:#2C3E50,stroke:#16A085,color:#fff
style PR fill:#2C3E50,stroke:#16A085,color:#fff
style DE fill:#2C3E50,stroke:#16A085,color:#fff
style RS fill:#2C3E50,stroke:#16A085,color:#fff
style RC fill:#2C3E50,stroke:#16A085,color:#fff
style GAP fill:#E67E22,stroke:#d35400,color:#fff
style PRIORITY fill:#16A085,stroke:#0e6655,color:#fff
How to use this assessment: 1. Rate each NIST function against the four maturity tiers 2. Identify functions at Tier 1 or Tier 2 as priority gaps 3. Allocate resources to bring lowest-maturity functions up first 4. A chain is only as strong as its weakest link - one Tier 1 function undermines Tier 4 elsewhere
1448.4.3 Real-World Example: Smart Factory Security
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'clusterBkg': '#f9f9f9', 'clusterBorder': '#2C3E50', 'edgeLabelBackground':'#ffffff'}}}%%
flowchart TB
subgraph Identify["1. IDENTIFY"]
A1[Inventory:<br/>500 IoT sensors<br/>50 PLCs<br/>10 robots]
A2[Critical Assets:<br/>Production line control<br/>Quality data]
end
subgraph Protect["2. PROTECT"]
B1[Network Segmentation:<br/>IoT VLAN isolated]
B2[Encryption:<br/>TLS for all data]
B3[Access Control:<br/>Role-based permissions]
end
subgraph Detect["3. DETECT"]
C1[IDS monitors<br/>unusual traffic]
C2[Anomaly detection<br/>on sensor data]
end
subgraph Respond["4. RESPOND"]
D1[Auto-isolate<br/>compromised device]
D2[Alert security team]
end
subgraph Recover["5. RECOVER"]
E1[Restore from backup]
E2[Patch vulnerability]
end
Identify --> Protect --> Detect --> Respond --> Recover
style Identify fill:#2C3E50,stroke:#16A085,color:#fff
style Protect fill:#16A085,stroke:#2C3E50,color:#fff
style Detect fill:#E67E22,stroke:#2C3E50,color:#fff
style Respond fill:#E67E22,stroke:#2C3E50,color:#fff
style Recover fill:#16A085,stroke:#2C3E50,color:#fff
1448.5 The McCumber Cube: 3D Security Model
The McCumber Cube extends the CIA triad across three data states (at rest, in transit, in use) and three countermeasure types (technology, policy, people), creating a comprehensive 3D security model with 27 control points.
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D', 'clusterBkg': '#f9f9f9', 'clusterBorder': '#2C3E50', 'edgeLabelBackground':'#ffffff'}}}%%
graph TB
subgraph "McCumber Cube: 3D Security Model"
subgraph "CIA Triad (Security Goals)"
C[Confidentiality]
I[Integrity]
A[Availability]
end
subgraph "Data States"
R[At Rest<br/>Storage]
T[In Transit<br/>Transmission]
P[In Use<br/>Processing]
end
subgraph "Countermeasures"
Tech[Technology<br/>Hardware/Software/Network]
Pol[Policy<br/>Procedures/Standards]
Ppl[People<br/>Training/Awareness]
end
end
C --> R
C --> T
C --> P
I --> R
I --> T
I --> P
A --> R
A --> T
A --> P
R --> Tech
R --> Pol
R --> Ppl
T --> Tech
T --> Pol
T --> Ppl
P --> Tech
P --> Pol
P --> Ppl
Total["27 Control Points<br/>(3 x 3 x 3)<br/>All must be addressed!"]
style C fill:#2C3E50,stroke:#16A085,color:#fff
style I fill:#2C3E50,stroke:#16A085,color:#fff
style A fill:#2C3E50,stroke:#16A085,color:#fff
style R fill:#16A085,stroke:#2C3E50,color:#fff
style T fill:#16A085,stroke:#2C3E50,color:#fff
style P fill:#16A085,stroke:#2C3E50,color:#fff
style Tech fill:#E67E22,stroke:#2C3E50,color:#fff
style Pol fill:#E67E22,stroke:#2C3E50,color:#fff
style Ppl fill:#E67E22,stroke:#2C3E50,color:#fff
style Total fill:#7F8C8D,stroke:#2C3E50,color:#fff
%% fig-alt: "McCumber Cube practical implementation checklist showing three parallel tracks for Technology, Policy, and People countermeasures."
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart TB
subgraph TECH["TECHNOLOGY CONTROLS (9 Points)"]
TR["AT REST:<br/>- AES-256 encryption<br/>- Access control lists<br/>- Integrity hashing"]
TT["IN TRANSIT:<br/>- TLS 1.3 / DTLS<br/>- Certificate pinning<br/>- VPN tunneling"]
TU["IN USE:<br/>- Secure enclaves (SGX)<br/>- Memory encryption<br/>- Input validation"]
end
subgraph POL["POLICY CONTROLS (9 Points)"]
PR["AT REST:<br/>- Data classification<br/>- Retention schedules<br/>- Backup procedures"]
PT["IN TRANSIT:<br/>- Acceptable use policy<br/>- Network standards<br/>- Partner agreements"]
PU["IN USE:<br/>- Processing procedures<br/>- Audit requirements<br/>- Access logging"]
end
subgraph PPL["PEOPLE CONTROLS (9 Points)"]
HR["AT REST:<br/>- Storage training<br/>- Clean desk policy<br/>- Device handling"]
HT["IN TRANSIT:<br/>- Phishing awareness<br/>- Secure messaging<br/>- Public Wi-Fi risks"]
HU["IN USE:<br/>- Shoulder surfing<br/>- Screen locking<br/>- Data disposal"]
end
TR --> CHECK1["C-I-A<br/>Verified"]
TT --> CHECK1
TU --> CHECK1
PR --> CHECK2["C-I-A<br/>Verified"]
PT --> CHECK2
PU --> CHECK2
HR --> CHECK3["C-I-A<br/>Verified"]
HT --> CHECK3
HU --> CHECK3
CHECK1 --> TOTAL["27/27 Controls<br/>FULLY PROTECTED"]
CHECK2 --> TOTAL
CHECK3 --> TOTAL
style TR fill:#16A085,stroke:#0e6655,color:#fff
style TT fill:#16A085,stroke:#0e6655,color:#fff
style TU fill:#16A085,stroke:#0e6655,color:#fff
style PR fill:#E67E22,stroke:#d35400,color:#fff
style PT fill:#E67E22,stroke:#d35400,color:#fff
style PU fill:#E67E22,stroke:#d35400,color:#fff
style HR fill:#2C3E50,stroke:#16A085,color:#fff
style HT fill:#2C3E50,stroke:#16A085,color:#fff
style HU fill:#2C3E50,stroke:#16A085,color:#fff
style TOTAL fill:#16A085,stroke:#0e6655,color:#fff
Quick Audit Checklist:
| Dimension | At Rest | In Transit | In Use |
|---|---|---|---|
| Technology | Encryption enabled? | TLS configured? | Secure memory? |
| Policy | Classification defined? | Transfer rules? | Processing procedures? |
| People | Storage training? | Secure comms? | Screen lock habits? |
Common Gaps by Organization Type: - Startups: Strong on Technology, weak on Policy and People (no formal processes) - Enterprises: Strong on Policy, weak on Technology modernization (legacy systems) - Government: Strong on Policy, moderate Technology, weak on People (bureaucratic training)
1448.6 Types of Security Controls
| Type | What It Is | IoT Examples |
|---|---|---|
| Technical | Technology solutions | Firewalls, encryption, authentication |
| Administrative | Policies and procedures | Password policy, security training, audits |
| Physical | Physical protection | Locked server room, secure device mounting |
All three are needed! Technical controls without policies = employees share passwords. Policies without technical = no enforcement.
Decision context: When allocating security resources for IoT systems, you must balance investment in preventive controls (stopping attacks before they succeed) against detective controls (identifying attacks that bypass prevention).
| Factor | Prevention-Focused | Detection-Focused |
|---|---|---|
| Complexity | High upfront design complexity | Requires ongoing monitoring infrastructure |
| Flexibility | Rigid rules may block legitimate use | Adapts to new attack patterns over time |
| Performance | May add latency (firewalls, encryption) | Minimal runtime impact, post-hoc analysis |
| Auditability | Limited visibility into blocked attempts | Rich forensic data for incident investigation |
Choose Prevention-Focused when: - Protecting life-critical systems (medical devices, industrial safety) - Zero-tolerance for specific attack types (ransomware, data exfiltration) - Regulatory requirements mandate specific controls (HIPAA, PCI-DSS) - Recovery from breach would be catastrophic or impossible
Choose Detection-Focused when: - Attack surface is too large to fully prevent all threats - Business agility requires flexible access policies - Insider threats are a significant concern - Budget constraints limit preventive infrastructure
Default recommendation: Defense-in-depth requires BOTH. Invest 60-70% in prevention (firewalls, encryption, access control, secure boot) and 30-40% in detection (IDS/IPS, SIEM, anomaly detection, audit logging). Assume prevention will eventually fail and ensure detection catches what slips through.
The Misconception: Many believe that implementing one robust security control (like strong encryption or a powerful firewall) provides adequate protection for IoT systems.
The Reality: Single-layer security fails catastrophically in real-world deployments.
Statistical Evidence: - IBM Cost of Data Breach 2023: Organizations with defense-in-depth saved $1.49M per breach vs single-layer security - Verizon DBIR 2023: 74% of breaches involved the human element - bypassing technical controls entirely - Ponemon Institute: Multi-layered security detected breaches 28 days faster (207 days vs 235 days mean time to identify)
Real IoT Failure Cases: - Mirai Botnet (2016): Strong network firewalls defeated by default passwords - 300,000+ IoT devices compromised - Stuxnet (2010): Air-gapped nuclear facility breached via USB - proved isolated technical control failed without policy enforcement - Target Breach (2013): Perimeter firewall intact, but HVAC vendor credentials enabled $202M breach
Why Single Layers Fail: 1. Zero-Day Vulnerabilities: Even perfect implementation has unknown flaws 2. Human Bypass: 82% of breaches involve phishing (Verizon 2023) 3. Configuration Errors: 95% of cloud breaches stem from customer misconfiguration 4. Lateral Movement: Without segmentation, attackers pivot from IoT to corporate networks
Bottom Line: NIST Framework defines five functions (not one) for a reason. Single-layer security is like a house with only a front door lock - first failure means total compromise.
1448.7 Knowledge Check: NIST Framework
1448.8 What’s Next
With the NIST Framework foundation established, the next chapter explores Security Control Implementation where you’ll learn to deploy intrusion detection systems for industrial IoT, configure role-based firewall policies for smart city networks, and implement technical controls that bring the NIST functions to life.
Continue to Security Control Implementation
Security Foundations: - Security Overview - Comprehensive security introduction - Encryption Principles - Cryptographic fundamentals - Threat Modelling - Identifying and mitigating threats
Implementation: - Security Control Implementation - IDS, firewall, and technical controls - Compliance and GDPR - Regulatory compliance for IoT
