%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22'}}}%%
flowchart TB
subgraph Device["Sensor Node"]
Reading[Sensor Reading]
DevKey[Unique Device Key<br/>AES-256]
Payload[Build Packet<br/>+Seq# +Checksum]
E2Enc[E2 Encrypt]
E1Enc[E1 Encrypt<br/>Shared key]
end
subgraph Router["Intermediate Router"]
E1Dec1[E1 Decrypt]
Forward[Forward Packet<br/>Cannot read payload]
E1Enc2[E1 Encrypt]
end
subgraph Gateway["Gateway"]
E1Dec2[E1 Decrypt]
E2Dec[E2 Decrypt<br/>Device-specific key]
Verify[Verify Seq#<br/>+ Checksum]
Store[(Device Key Store)]
end
Reading --> Payload
DevKey -.-> E2Enc
Payload --> E2Enc --> E1Enc
E1Enc --> E1Dec1 --> Forward --> E1Enc2
E1Enc2 --> E1Dec2 --> E2Dec
Store -.->|Lookup device key| E2Dec
E2Dec --> Verify
style Device fill:#2C3E50,stroke:#16A085,stroke-width:2px,color:#fff
style Router fill:#E67E22,stroke:#2C3E50,stroke-width:2px,color:#fff
style Gateway fill:#16A085,stroke:#2C3E50,stroke-width:2px,color:#fff
1427 E2: Device-to-Gateway Encryption
1427.1 Learning Objectives
By the end of this chapter, you will be able to:
- Implement E2 Device-to-Gateway Encryption: Design per-device key architectures with AES-256
- Configure Replay Attack Protection: Implement sequence numbers and checksums for message integrity
- Design E2 Packet Structures: Build secure packet formats with proper authentication
- Choose Between E2 and E3: Determine when to use gateway-terminated vs end-to-end encryption
1427.2 Introduction to E2 Device-to-Gateway Encryption
E2 (Device-to-Gateway) encryption ensures authenticity and prevents intermediate nodes from reading data using unique per-device keys.
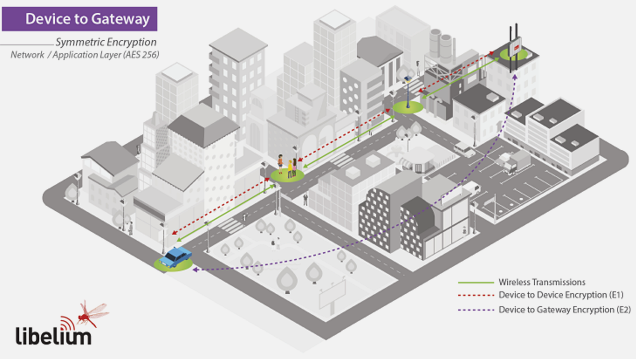
Purpose: Ensure authenticity and prevent intermediate nodes from reading data.
Characteristics:
- Each node has unique private key
- Gateway stores all node keys
- AES-256 encryption at application layer
- Combined with E1 (double encryption)
- Includes sequence number + checksum for integrity
1427.3 E2 Implementation Details
Algorithm: AES-256 in CBC mode with integrity protection
Packet Structure:
%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22'}}}%%
graph LR
subgraph Packet["E2 Encrypted Packet"]
IV[IV<br/>16 bytes<br/>Random]
Header[Device ID<br/>16 bytes]
Seq[Sequence #<br/>4 bytes]
Data[Payload<br/>Variable]
Hash[SHA-256<br/>32 bytes<br/>Integrity]
end
IV --> Header --> Seq --> Data --> Hash
style IV fill:#E67E22,stroke:#2C3E50,stroke-width:2px,color:#fff
style Header fill:#2C3E50,stroke:#16A085,stroke-width:2px,color:#fff
style Seq fill:#2C3E50,stroke:#16A085,stroke-width:2px,color:#fff
style Data fill:#16A085,stroke:#2C3E50,stroke-width:2px,color:#fff
style Hash fill:#7F8C8D,stroke:#2C3E50,stroke-width:2px,color:#fff
Key Characteristics:
| Aspect | Details |
|---|---|
| Key Size | 256 bits (32 bytes) - unique per device |
| Authentication | SHA-256 checksum + sequence number |
| Replay Protection | Monotonically increasing sequence numbers |
| Key Storage | Gateway maintains database of device keys |
| Integrity | Hash verification detects tampering |
Security Properties:
- Device Authentication: Each device has unique key
- Data Integrity: SHA-256 detects modifications
- Replay Protection: Sequence numbers prevent replay attacks
- Intermediate Node Security: Routers cannot read payload
- Key Management Complexity: Gateway must store N device keys
Attack Mitigations:
| Attack Type | Mitigation |
|---|---|
| Replay Attack | Sequence number validation - gateway rejects old sequences |
| Tampering | SHA-256 checksum - any modification invalidates hash |
| Spoofing | Unique device keys - attacker cannot impersonate without key |
| Man-in-Middle | Combined with E1 - ensures packet origin authenticity |
1427.4 E2 vs E3: When to Use Each
Option A (E2 - Device-Gateway): Gateway decrypts data for local processing, enables edge analytics (reduce cloud bandwidth by 60-80%), allows gateway-based anomaly detection, requires trusted gateway hardware, 5-10ms processing latency at gateway.
Option B (E3 - End-to-End): Data encrypted from device to cloud, gateway only forwards opaque packets, zero-trust architecture (gateway compromise doesn’t leak data), prevents edge processing, adds 2-5ms encryption overhead per hop.
Decision Factors: Choose E2 when gateway is physically secured and local processing reduces bandwidth costs (industrial monitoring, smart buildings). Choose E3 when gateway is in semi-public location (retail, outdoor), when regulatory compliance requires end-to-end encryption (HIPAA, PCI-DSS), or when gateway vendor isn’t fully trusted.
1427.5 E1-E5 Benefits Mapping
Each encryption level (E1-E5) solves specific security problems. Understanding the mapping helps you choose the right combination:
| Level | Encrypts | Security Guarantee | Threat Mitigated |
|---|---|---|---|
| E1 | Link layer | Access control | Unauthorized network join |
| E2 | Device-Gateway | Authentication + Confidentiality | Eavesdropping on local network |
| E3 | Device-Cloud | End-to-end confidentiality | Untrusted gateway |
| E4 | Gateway-Cloud | Web-grade TLS | Internet eavesdropping |
| E5 | Key renewal | Long-term key freshness | Key compromise over time |
1427.5.1 Common Combinations
| Scenario | Recommended Levels | Why |
|---|---|---|
| Trusted gateway | E1 + E2 + E4 | Gateway can decrypt; cloud link protected |
| Untrusted gateway | E1 + E3 + E4 | Data stays encrypted through gateway |
| Long deployment | + E5 | Keys rotated to prevent compromise |
1427.5.2 Key Insight: The Untrusted Gateway Problem
In many IoT deployments, the gateway may be in a semi-public location (factory floor, retail store). Using E3 instead of E2 means:
- Gateway cannot read sensor data (only forwards encrypted packets)
- Compromised gateway cannot leak sensitive information
- Trade-off: Gateway cannot do local processing/filtering
1427.6 Encryption Layer Selection
This decision tree helps select appropriate encryption layers based on deployment characteristics:
%%{init: {'theme': 'base', 'themeVariables': { 'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#16A085', 'secondaryColor': '#E67E22', 'tertiaryColor': '#7F8C8D'}}}%%
flowchart TD
START["SELECT ENCRYPTION<br/>LAYERS"] --> Q1{Data<br/>Sensitive?}
Q1 -->|No| E1["E1 ONLY<br/>Link layer AES-128<br/>Basic protection"]
Q1 -->|Yes| Q2{Gateway<br/>Trusted?}
Q2 -->|Yes| E12["E1 + E2<br/>Link + Device-Gateway<br/>Gateway can process"]
Q2 -->|No| E13["E1 + E3<br/>Link + End-to-End<br/>Gateway blind"]
E12 --> Q3{Internet<br/>Transit?}
E13 --> Q3
Q3 -->|No| CHECK_TIME
Q3 -->|Yes| E4["ADD E4<br/>TLS 1.3 transport<br/>Certificate auth"]
E4 --> CHECK_TIME{Deployment<br/>2+ years?}
CHECK_TIME -->|No| DONE["COMPLETE<br/>Selected layers"]
CHECK_TIME -->|Yes| E5["ADD E5<br/>Key renewal<br/>RSA/ECDH rotation"]
E5 --> DONE
style START fill:#2C3E50,stroke:#16A085,color:#fff
style Q1 fill:#E67E22,stroke:#d35400,color:#fff
style Q2 fill:#E67E22,stroke:#d35400,color:#fff
style Q3 fill:#E67E22,stroke:#d35400,color:#fff
style CHECK_TIME fill:#E67E22,stroke:#d35400,color:#fff
style E1 fill:#16A085,stroke:#0e6655,color:#fff
style E12 fill:#16A085,stroke:#0e6655,color:#fff
style E13 fill:#16A085,stroke:#0e6655,color:#fff
style E4 fill:#16A085,stroke:#0e6655,color:#fff
style E5 fill:#16A085,stroke:#0e6655,color:#fff
style DONE fill:#2C3E50,stroke:#16A085,color:#fff
Quick Reference Combinations:
| Scenario | Layers | Example Use Case |
|---|---|---|
| Trusted home network | E1 | Smart light bulbs |
| Industrial with trusted gateway | E1 + E2 + E4 | Factory sensors to cloud |
| Medical device, untrusted network | E1 + E3 + E4 + E5 | Remote patient monitoring |
| Critical infrastructure | E1 + E3 + E4 + E5 | Smart grid, water treatment |
1427.7 Knowledge Check: Encryption Layers
Knowledge Check: Encryption Layers E1-E5 Quick Check
Concept: Understanding which encryption layer to use based on trust model and data sensitivity.
A hospital deploys patient monitoring sensors in semi-public areas. The gateway is physically accessible to unauthorized personnel. Which encryption layer combination best protects patient data?
C is correct. With an untrusted gateway in a semi-public location, E3 (end-to-end) ensures the gateway cannot decrypt patient data - it only forwards encrypted packets. E1 provides local link protection, E4 secures internet transit, and E5 ensures long-term key freshness for HIPAA compliance. E2 would allow the gateway to decrypt data, which is unacceptable in this threat model.
What is the primary difference between E2 (device-to-gateway) and E3 (device-to-cloud) encryption?
B is correct. The key distinction is WHERE decryption occurs. E2 terminates at the gateway, allowing edge processing and filtering. E3 encrypts directly to the cloud, making the gateway “blind” to the payload - ideal for zero-trust architectures where gateway compromise shouldn’t leak data.
Option A (Full Payload Encryption): Encrypt entire message body (header + data), maximum confidentiality, 100% overhead on payload size with authenticated encryption modes, gateway cannot route based on content, simpler key management (one key per device-cloud pair).
Option B (Selective Field Encryption): Encrypt only sensitive fields (e.g., patient vitals, GPS coordinates), routing metadata remains readable, 20-40% overhead on sensitive fields only, enables edge-based filtering and aggregation, requires field-level key management (complexity 3x higher).
Decision Factors: Choose full encryption for high-security applications where any metadata leakage is unacceptable (medical devices, personal tracking). Choose selective encryption when edge processing is critical and only specific fields contain sensitive data (smart meters where timestamps are public but usage is private, fleet tracking where route is sensitive but vehicle status is not).
1427.8 Summary
This chapter covered E2 device-to-gateway encryption:
- E2 Purpose: Per-device keys ensure authenticity and prevent intermediate nodes from reading data
- Packet Structure: Device ID + sequence number + encrypted payload + SHA-256 checksum
- Replay Protection: Monotonically increasing sequence numbers prevent replay attacks
- E2 vs E3: Use E2 when gateway is trusted and needs to process data locally; use E3 for untrusted gateways
- Key Management: Gateway must securely store unique keys for each device in the network
1427.9 What’s Next
Continue to E3-E4: Transport and End-to-End Encryption to learn how device-to-cloud encryption (E3) enables use of untrusted gateways, and how TLS (E4) provides industry-standard transport security.
- E1: Link Layer Encryption - Foundation of IoT encryption
- E3-E4: Transport and End-to-End - Cloud communication security
- E5: Key Renewal - Long-term key management
- Encryption Architecture Overview - Five-layer framework
