%%{init: {'theme': 'base', 'themeVariables': {'primaryColor': '#2C3E50', 'primaryTextColor': '#fff', 'primaryBorderColor': '#16A085', 'lineColor': '#E67E22', 'secondaryColor': '#16A085', 'tertiaryColor': '#E67E22', 'clusterBkg': '#f9f9f9', 'clusterBorder': '#2C3E50', 'fontSize': '13px'}}}%%
graph TB
CTRL[SDN Controller]
subgraph Switch["OpenFlow Switch"]
CHANNEL[Secure Channel<br/>TLS/SSL]
FLOW[Flow Tables<br/>Match + Actions]
GROUP[Group Table<br/>Multi-output]
METER[Meter Table<br/>Rate Limiting]
BUFFER[Packet Buffer<br/>Temporary Storage]
PORTS[Physical Ports<br/>Network Interfaces]
end
CTRL <-->|OpenFlow Protocol| CHANNEL
CHANNEL --> FLOW
CHANNEL --> GROUP
CHANNEL --> METER
FLOW --> BUFFER
GROUP --> PORTS
METER --> PORTS
BUFFER --> PORTS
PORTS -->|Packets In| FLOW
PORTS -->|Packets Out| BUFFER
style CTRL fill:#2C3E50,stroke:#16A085,color:#fff
style CHANNEL fill:#E67E22,stroke:#2C3E50,color:#fff
style FLOW fill:#16A085,stroke:#2C3E50,color:#fff
style GROUP fill:#16A085,stroke:#2C3E50,color:#fff
style PORTS fill:#16A085,stroke:#2C3E50,color:#fff
286 OpenFlow Protocol and Flow Tables
286.1 Learning Objectives
By the end of this chapter, you will be able to:
- Understand OpenFlow Protocol: Explain how OpenFlow enables controller-switch communication and flow rule installation
- Design Flow Table Entries: Create match-action rules with appropriate priorities, timeouts, and counters
- Program Network Policies: Use OpenFlow messages (PACKET_IN, FLOW_MOD, STATS) to implement network behavior
- Address SDN Challenges: Mitigate scalability, security, and reliability issues in SDN-based IoT deployments
Core concept: OpenFlow is the standardized protocol enabling SDN controllers to program switches with flow rules - each rule specifies what packet headers to match and what action to take (forward, drop, modify). Why it matters: Flow tables enable wire-speed packet forwarding (nanoseconds) because switches make forwarding decisions locally using pre-installed rules, rather than asking the controller for every packet. Key takeaway: Design flow rules with appropriate timeouts - idle timeouts for dynamic traffic (rules expire when unused) and hard timeouts for security-sensitive flows (force periodic re-authorization from controller).
286.2 Prerequisites
- SDN Core Concepts: Understanding of control/data plane separation
- SDN Architecture: Knowledge of three-layer architecture and controller design
286.3 OpenFlow Protocol Overview
OpenFlow is the standardized southbound protocol for communication between controller and switches.
286.4 OpenFlow Switch Components
{fig-alt=“OpenFlow switch components diagram showing SDN controller connecting via OpenFlow protocol to secure channel (TLS/SSL), which manages flow tables (match + actions), group table (multi-output), meter table (rate limiting), packet buffer (temporary storage), and physical ports (network interfaces) with bidirectional packet flow”}
Core Concept: A flow table is a list of match-action rules stored in switch memory that determines how packets are forwarded without consulting the controller. Why It Matters: Flow tables enable wire-speed packet forwarding (nanoseconds) because switches make forwarding decisions locally using pre-installed rules, rather than asking the controller for every packet (which would add 10-50ms latency). Key Takeaway: Design flow rules with appropriate timeouts - idle timeouts for dynamic traffic (rules expire when unused) and hard timeouts for security-sensitive flows (force periodic re-authorization from controller).
286.5 Flow Table Entry Structure
Each flow entry contains:
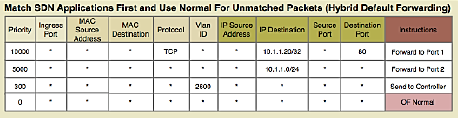
1. Match Fields (Packet Header Fields): - Layer 2: Source/Dest MAC, VLAN ID, Ethertype - Layer 3: Source/Dest IP, Protocol, ToS - Layer 4: Source/Dest Port (TCP/UDP) - Input Port - Metadata
2. Priority: - Higher priority rules matched first - Allows specific rules to override general rules
3. Counters: - Packets matched - Bytes matched - Duration
4. Instructions/Actions: - Forward to port(s) - Drop - Modify header fields (MAC, IP, VLAN) - Push/Pop VLAN/MPLS tags - Send to controller - Go to next table
5. Timeouts: - Idle Timeout: Remove rule if no matching packets for N seconds - Hard Timeout: Remove rule after N seconds regardless of activity
6. Cookie: - Opaque identifier set by controller
Example Flow Rule:
Match: src_ip=10.0.0.5, dst_ip=192.168.1.10, protocol=TCP, dst_port=80
Priority: 100
Actions: output:port3, set_vlan=100
Idle_timeout: 60
Hard_timeout: 300286.6 Knowledge Check
Test your understanding of OpenFlow concepts.
286.7 Common Misconceptions About SDN
Misconception 1: “SDN makes all switches dumb - they just forward blindly”
Reality: OpenFlow switches are intelligent forwarding devices with sophisticated match-action tables, group tables for multicast, meter tables for QoS, and local packet buffers. They make fast forwarding decisions in hardware using TCAM (Ternary Content Addressable Memory). The controller programs the “what” (flow rules), but switches optimize the “how” (wire-speed forwarding).
Misconception 2: “The SDN controller handles every packet”
Reality: Only first packets of new flows (table misses) go to the controller via PACKET_IN messages. The controller installs flow rules, then switches handle all subsequent packets of that flow in hardware at line rate (Gbps/Tbps speeds). Controllers see configuration traffic, not data plane traffic. A well-designed SDN uses proactive rules (pre-installed) to minimize controller involvement.
Misconception 3: “SDN is only for data centers and enterprises, not for IoT”
Reality: SDN is highly valuable for IoT networks: - Wireless Sensor Networks: Centralized routing optimization for energy efficiency - Smart Cities: Dynamic traffic prioritization (emergency vehicles, traffic lights) - Industrial IoT: QoS guarantees for time-critical machine control - LPWAN: Gateway coordination and spectrum management - Edge Computing: Dynamic workload placement and traffic steering
Misconception 4: “OpenFlow is the only SDN southbound protocol”
Reality: While OpenFlow is the most common standardized protocol, SDN supports multiple southbound APIs: - NETCONF/YANG: Configuration management for network devices - P4: Programmable data plane (define custom packet processing) - gRPC/gNMI: Google’s network management interfaces - OVSDB: Open vSwitch database management - BGP/PCEP: Integration with existing routing protocols
Misconception 5: “SDN eliminates all network security concerns”
Reality: SDN introduces new attack vectors: - Controller compromise: Attacker gains network-wide control - Controller-switch channel: Must use TLS to prevent MITM attacks - Northbound API: Need authentication/authorization for applications - Flow rule manipulation: Malicious apps could install harmful rules - DDoS on controller: Flood with PACKET_IN messages (table-miss attacks)
Best practices: Strong authentication, network segmentation, RBAC, controller clustering, and flow rule validation.
286.8 Cross-Hub Connections
Interactive Simulations: - Simulations Hub - Network topology visualizer shows SDN control flow - Try designing an SDN topology for a smart building with mixed device types
Knowledge Checks: - Quizzes Hub - OpenFlow protocol exercises - Test your understanding of flow table matching and priority rules
Video Tutorials: - Videos Hub - SDN controller programming tutorials - Watch practical demonstrations of OpenDaylight and Ryu controllers
Common Gaps: - Knowledge Gaps Hub - “Why centralized control doesn’t mean single point of failure” - Understanding controller clustering and high availability architectures
286.9 Visual Reference Gallery
286.10 Summary
This chapter explored the OpenFlow protocol and flow tables:
- OpenFlow Protocol: Standardized southbound protocol enabling controllers to install flow rules in switches via messages like PACKET_IN, FLOW_MOD, and STATS
- Flow Table Structure: Match fields (L2-L4 headers), priority, counters, actions (forward/drop/modify), timeouts (idle/hard), and cookies for controller identification
- Switch Components: Flow tables, group tables (multicast/load balancing), meter tables (rate limiting), packet buffers, and secure TLS channel to controller
- SDN Security: Controller compromise affects entire network - requires strong authentication, network segmentation, RBAC, and clustering
- Common Misconceptions: Switches are intelligent forwarding devices, controllers only handle first packets, SDN applies well to IoT networks
286.11 What’s Next
The next chapter provides a Hands-On Lab with an ESP32-based SDN controller simulation, demonstrating flow table management, PACKET_IN/FLOW_MOD message handling, and priority-based QoS.








