265 Mobile Computing Challenges and Network Architectures
265.1 Learning Objectives
By the end of this chapter, you will be able to:
- Manage Power Constraints: Balance gateway functionality with mobile device battery limitations
- Handle Connectivity Challenges: Design for intermittent, heterogeneous network conditions
- Evaluate Network Architectures: Compare infrastructure-based and ad-hoc mobile networks
- Design for Mobility: Implement solutions that handle device movement and topology changes
265.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- Mobile Gateway Fundamentals: Understanding basic gateway roles and limitations
- Mobile Gateway Edge and Fog: Knowledge of edge/fog processing patterns
- Duty Cycling: Alternating between active and sleep modes to conserve battery
- Store-and-Forward: Buffering data locally during connectivity outages
- Network Heterogeneity: Managing connections across Wi-Fi, cellular, and Bluetooth simultaneously
- Ad-hoc Networks: Self-organizing networks without fixed infrastructure
- MANET: Mobile Ad-hoc Network - devices communicating directly without central coordination
265.3 Fundamental Challenges in Mobile Computing
Mobile computing introduces unique challenges that impact IoT implementations using mobile phones as infrastructure components.
265.3.1 Resource Constraints
Limited Battery Life: Mobile devices operate on battery power, creating fundamental tradeoffs between functionality and energy consumption.
Mitigation Strategies: - Duty cycling: Alternating between active and sleep modes - Adaptive sensing: Adjusting sampling rates based on context - Energy-efficient algorithms: Optimizing computation for minimal power consumption - Offloading: Delegating intensive tasks to cloud or nearby infrastructure when beneficial
Processing Limitations: Despite improvements, mobile processors have limited computational capacity compared to cloud servers or desktop systems.
Mitigation Strategies: - Edge-cloud collaboration: Partitioning tasks between local and remote processing - Lightweight algorithms: Using simplified models suitable for mobile constraints - Hardware acceleration: Leveraging specialized chips (AI accelerators, GPUs)
Storage Constraints: Mobile devices have limited storage compared to cloud systems, constraining local data retention.
Mitigation Strategies: - Intelligent caching: Keeping only essential data locally - Compression: Reducing data size before storage - Tiered storage: Using cloud for archival, local for active data
265.3.2 Connectivity Challenges
Network Heterogeneity: Mobile devices connect through multiple, changing networks (Wi-Fi, 4G, 5G, Bluetooth) with varying characteristics.
Challenges: - Seamless handoff between network types - Maintaining connections during transitions - Adapting to bandwidth and latency variations - Managing connectivity costs (data plans)
Intermittent Connectivity: Mobile devices frequently lose network connectivity due to movement, obstacles, or network congestion.
Mitigation Strategies: - Offline capabilities: Functioning without continuous connectivity - Store-and-forward: Queuing data for transmission when connectivity resumes - Opportunistic networking: Using available connectivity windows efficiently
Variable Network Quality: Signal strength, bandwidth, and latency vary significantly based on location and network load.
Adaptation Strategies: - Adaptive bitrate: Adjusting data transmission rates based on network conditions - Protocol selection: Choosing appropriate protocols for current network state - Predictive pre-loading: Anticipating connectivity gaps and pre-fetching data
265.3.3 Mobility Management
Location Variability: Mobile devices constantly change location, requiring dynamic service discovery and adaptation.
Challenges: - Maintaining service continuity during movement - Discovering local IoT devices and services - Context adaptation based on location changes
Dynamic Topologies: Network topology changes as devices move, requiring robust routing and discovery protocols.
265.4 Challenges in Designing Mobile Computing Systems
Designing effective mobile computing systems for IoT applications requires addressing multiple architectural and operational challenges.
265.4.1 User Experience Considerations
Interface Design: Mobile interfaces must be intuitive despite small screen sizes and varied user contexts (walking, driving, multitasking).
Design Principles: - Simplicity: Minimal steps to accomplish tasks - Context awareness: Adapting interface based on user situation - Feedback: Clear indication of system status and actions - Error prevention: Designing to minimize user mistakes
Performance Expectations: Users expect instant responsiveness despite computational and network limitations.
Strategies: - Optimistic UI: Showing results immediately while processing in background - Progressive enhancement: Displaying basic information quickly, details later - Skeleton screens: Visual placeholders during loading
265.4.2 Security and Privacy
Multi-Tenant Environments: Personal devices hosting IoT applications raise security concerns about data isolation and access control.
Security Requirements: - Data encryption: Protecting data at rest and in transit - Authentication: Verifying user and device identities - Authorization: Controlling access to resources and data - Secure updates: Protecting against malicious software updates
Privacy Concerns: Mobile IoT applications collect sensitive personal data (location, health, behavior), raising privacy issues.
Privacy Protection Measures: - Data minimization: Collecting only necessary data - User consent: Transparent permission requests - Anonymization: Removing personally identifiable information - Local processing: Keeping sensitive data on-device when possible
265.4.3 Application Development Complexity
Platform Fragmentation: Developing for multiple mobile platforms (iOS, Android) with different capabilities and APIs increases complexity.
Approaches: - Cross-platform frameworks: React Native, Flutter, Xamarin - Progressive web apps: Web-based applications with native-like capabilities - Platform-specific optimization: Tailoring experiences to each platform
Version Diversity: Supporting various OS versions with different features and APIs is challenging.
Strategies: - Graceful degradation: Providing basic functionality on older versions - Feature detection: Dynamically adapting to available capabilities - Minimum version requirements: Focusing development on recent versions
265.5 Infrastructure-based vs Ad-hoc Mobile Networks
Mobile IoT systems can operate using different network architectures, each with distinct characteristics and use cases.
265.5.1 Infrastructure-based Networks
Infrastructure-based networks rely on fixed network infrastructure (cell towers, Wi-Fi access points) to facilitate communication.
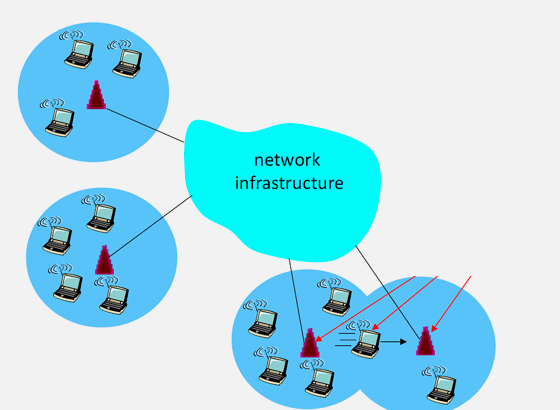
Characteristics: - Centralized Control: Network managed by service providers - Fixed Access Points: Devices connect through established infrastructure - Reliable Coverage: Predictable service in covered areas - Scalability: Supports large numbers of devices - Quality of Service: Managed bandwidth and priority
Examples: - Cellular networks (4G/5G) for wide-area IoT connectivity - Wi-Fi networks in smart homes and buildings - Dedicated IoT networks (NB-IoT, LTE-M)
Advantages: - Reliable, managed connectivity - Wide coverage areas - Quality of service guarantees - Well-established protocols and standards - Professional network management
Disadvantages: - Infrastructure deployment costs - Dependency on service providers - Limited flexibility in remote areas - Potential single points of failure - Ongoing operational costs
IoT Use Cases: - Smart city infrastructure monitoring - Connected vehicle telematics - Industrial IoT with cloud connectivity - Remote patient monitoring - Fleet management and logistics
265.5.2 Ad-hoc Networks
Ad-hoc networks form spontaneously without fixed infrastructure, with devices communicating directly or through multi-hop routing.

Characteristics: - Decentralized: No central coordination required - Self-Organizing: Network topology adapts dynamically - Peer-to-Peer: Devices communicate directly or through intermediaries - Temporary: Networks form and dissolve as needed - Autonomous: Independent of infrastructure
Types of Ad-hoc Networks:
Mobile Ad-hoc Networks (MANETs): Self-configuring networks of mobile devices connected via wireless links.
Vehicular Ad-hoc Networks (VANETs): Networks formed by vehicles communicating for safety and traffic management.
Wireless Sensor Networks (WSNs): Networks of sensor nodes collaborating for environmental monitoring or tracking.
Opportunistic Networks: Networks exploiting brief contact opportunities between mobile devices.
Advantages: - Rapid deployment without infrastructure - Flexibility in dynamic environments - Cost-effective for temporary applications - Resilience through distributed operation - Privacy through local communication
Disadvantages: - Limited range and scalability - Variable connectivity and reliability - Higher battery consumption (routing overhead) - Security vulnerabilities - Complex routing protocols
IoT Use Cases: - Disaster response and emergency networks - Temporary event monitoring (concerts, sports events) - Collaborative mobile sensing - Wildlife tracking in remote areas - Peer-to-peer smart home device communication
265.5.3 Hybrid Approaches
Many modern IoT systems combine infrastructure-based and ad-hoc networking to leverage advantages of both approaches.
Option A: Infrastructure-Based Networks - Rely on fixed infrastructure (cell towers, Wi-Fi access points) for centralized, reliable connectivity with managed QoS.
Option B: Ad-Hoc Networks - Form spontaneous peer-to-peer networks without fixed infrastructure, enabling rapid deployment and resilience through distributed operation.
Decision Factors:
Choose Infrastructure-Based when: Reliable coverage is available, QoS guarantees are needed (latency, bandwidth), scale requires professional management, or ongoing connectivity costs are acceptable.
Choose Ad-Hoc when: Infrastructure doesn’t exist (disaster response, remote wilderness), temporary deployment is needed (events, construction sites), privacy requires avoiding centralized collection, or cost constraints prohibit infrastructure subscription fees.
Consider Hybrid when: Primary infrastructure provides reliable baseline while ad-hoc capabilities handle edge cases (D2D communication for nearby devices, mesh fallback during outages). 5G networks increasingly support both modes natively.
Examples: - Mesh Wi-Fi Networks: Combining infrastructure access points with mesh networking for extended coverage - Bluetooth Mesh: Devices form mesh networks while maintaining cloud connectivity through gateways - Cellular-D2D: 5G networks supporting both infrastructure and direct device-to-device communication - Fog-Cloud Hybrid: Local ad-hoc processing with cloud synchronization when connectivity available
265.6 Knowledge Check
265.7 Summary
This chapter examined fundamental challenges in mobile computing:
- Resource Constraints: Battery life requires duty cycling (33% active time extends operation), processing limitations need edge-cloud collaboration, storage constraints require intelligent caching
- Connectivity Challenges: Network heterogeneity (Wi-Fi saves 63% battery vs cellular), intermittent connectivity needs store-and-forward buffering, variable quality requires adaptive protocols
- Infrastructure vs Ad-hoc: Infrastructure provides reliable managed connectivity; ad-hoc enables rapid deployment without fixed hardware; hybrid approaches combine both advantages
- Design Considerations: UX requires optimistic UI and progressive enhancement; security needs encryption and authentication; platform fragmentation addressed through cross-platform frameworks
265.8 What’s Next?
The next chapter covers wireless medium access control protocols, communication technologies, best practices, and a hands-on lab for building an IoT gateway.
