468 M2M Service Platforms and Network Architectures
468.1 Learning Objectives
By the end of this chapter, you will be able to:
- Design M2M Service Platforms: Configure the four-layer M2SP architecture
- Compare Network Architectures: Distinguish between IP-based and non-IP M2M networks
- Apply ETSI Requirements: Implement scalability, anonymity, and scheduling standards
- Select Delivery Methods: Choose appropriate unicast, multicast, anycast, or broadcast patterns
468.2 Prerequisites
Before diving into this chapter, you should be familiar with:
- M2M Communication Overview: Introduction to machine-to-machine concepts
- M2M Applications and Node Types: Understanding M2M use cases and device hierarchy
- Networking Basics for IoT: Network protocols and addressing
468.3 Introduction
Think of an M2M Service Platform like a hotel management system:
- Device Platform = Front desk (registers guests/devices, manages check-in/out)
- User Platform = Membership system (who can access what rooms/devices)
- Application Platform = Concierge service (coordinates activities, provides analytics)
- Access Platform = Building management (HVAC, elevators, security - the infrastructure)
Without a platform, managing thousands of devices would be like running a hotel without any management software - chaos!
The M2M Service Platform provides the middleware infrastructure enabling device management, user authentication, application orchestration, and network access at scale.
468.4 M2M Service Platform (M2SP)
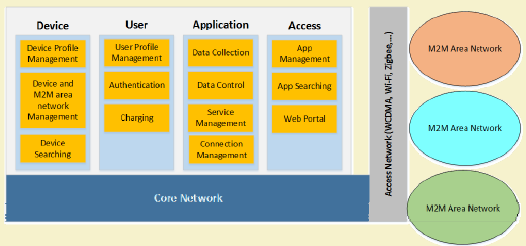
The M2M Service Platform provides the middleware infrastructure for M2M applications, abstracting device heterogeneity and enabling service composition.
468.4.1 Device Platform
Responsibilities: - Device registration and lifecycle management - Device profile management (type, location, capabilities) - Authentication and authorization - Monitoring and control - Firmware updates
Key Operations: - Onboarding: Provision new devices securely - Discovery: Locate devices by capability or location - Configuration: Push settings and parameters - Diagnostics: Query device health remotely
468.4.2 User Platform
Responsibilities: - User registration and profile management - Access control (which users can access which devices) - Billing and charging - Administrative privileges
Access Control Model: - Role-based access control (RBAC) - Device-level permissions - Time-based access restrictions - Audit logging for compliance
468.4.3 Application Platform
Responsibilities: - Service orchestration (compose services from multiple devices) - Data integration from heterogeneous sources - Analytics and intelligence - Connection management
Capabilities: - Event processing and alerting - Data transformation and normalization - API management for third-party access - Machine learning inference
468.4.4 Access Platform
Responsibilities: - Web and mobile app hosting - API gateway for external access - App management (registration, versioning) - Device-app mapping
468.5 M2M Network Architectures
468.5.1 Non-IP Based M2M Network
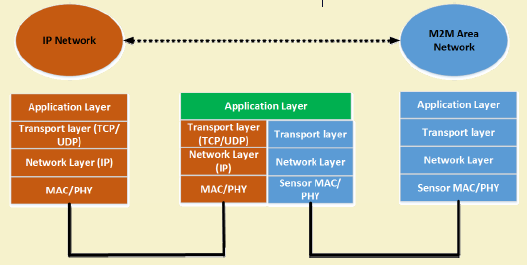
Legacy M2M networks often use proprietary protocols without IP layer.
Characteristics: - Proprietary protocols (Modbus, BACnet, HART) - Limited interoperability - Gateway required for internet connectivity - Common in industrial automation
When to Use Non-IP: - Legacy industrial equipment - Ultra-low power requirements - Air-gapped security requirements - Specialized industrial protocols
468.5.2 IP-Based M2M Network
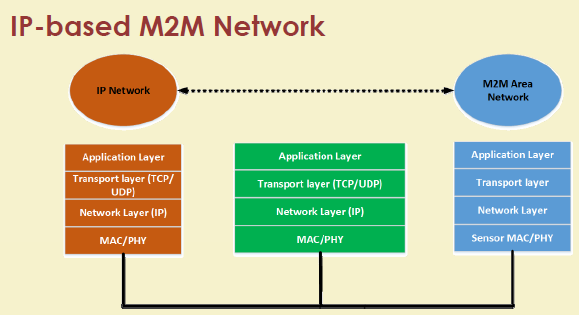
Modern M2M leverages IP connectivity end-to-end.
Characteristics: - Standard protocols (IPv6, 6LoWPAN, CoAP, MQTT) - Direct internet connectivity - Interoperable - Cloud-native
When to Use IP-Based: - Cloud connectivity required - Multi-vendor interoperability - Standard monitoring tools - Developer ecosystem access
468.6 M2M Requirements (ETSI Standards)
The European Telecommunications Standards Institute (ETSI) defines comprehensive M2M system requirements:
468.6.1 1. Scalability
- Support millions of connected devices
- Efficient resource allocation as network grows
- Distributed architecture for horizontal scaling
468.6.2 2. Anonymity
- Hide device identity when required (privacy)
- Support pseudonymous communication
- Comply with regulatory requirements (GDPR)
468.6.3 3. Logging and Auditing
- Record important events (failures, security incidents)
- Tamper-proof logs for compliance
- Accessible for forensics and debugging
468.6.4 4. Communication Principles
- Support diverse communication techniques:
- SMS for command and control
- IP for data streaming
- Peer-to-peer for local coordination
- Multiple transport protocols (TCP, UDP, CoAP, MQTT)
468.6.5 5. Delivery Methods
- Unicast: One-to-one communication
- Multicast: One-to-many (group communication)
- Anycast: One-to-nearest (server selection)
- Broadcast: One-to-all (minimize when possible)
468.6.6 6. Message Scheduling
- Control network access to prevent congestion
- Schedule non-urgent messages during off-peak
- Respect application delay tolerance
468.6.7 7. Communication Path Selection
- Optimize paths based on:
- Transmission failures (avoid bad links)
- Delays (minimize latency)
- Network costs (prefer Wi-Fi over cellular)
- Support multi-path communication
468.7 Knowledge Check
468.8 Visual Reference Gallery
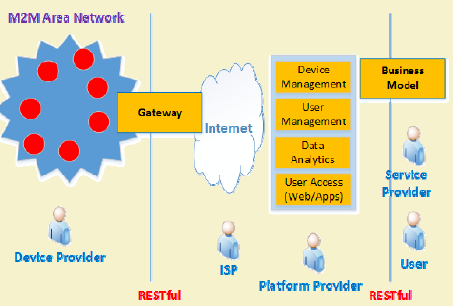
The M2M reference architecture organizes communication infrastructure into device, network, and application domains with standardized interfaces.
M2M gateways bridge the gap between resource-constrained local networks and IP-based wide area networks, enabling seamless device integration.
468.9 Summary
This chapter explored M2M Service Platforms and network architectures:
Key Takeaways:
M2M Service Platform (M2SP): Four-layer architecture (Device, User, Application, Access) provides complete M2M lifecycle management
Network Evolution: From proprietary non-IP M2M to IP-based M2M enabling internet connectivity and interoperability
ETSI Requirements: Scalability, anonymity, logging, diverse communication modes, scheduling, path optimization
Delivery Methods: Unicast, multicast, anycast, and broadcast serve different communication patterns
Platform APIs: RESTful APIs, WebSocket events, OAuth2 authentication enable third-party integration
468.10 What’s Next?
Building on M2M platforms and network architectures, the next chapter explores hands-on M2M implementations and comprehensive knowledge assessment.
Continue to M2M Labs and Assessment →
- M2M Communication Overview - Introduction and key concepts
- M2M Applications and Node Types - Industry applications
- M2M Labs and Assessment - Hands-on implementation
- Edge-Fog-Cloud Computing - Multi-tier M2M deployments



